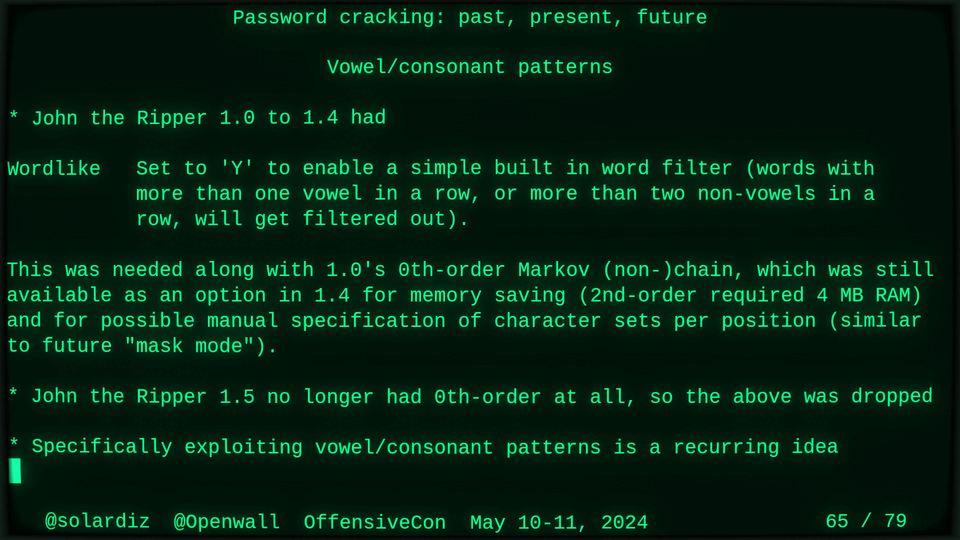
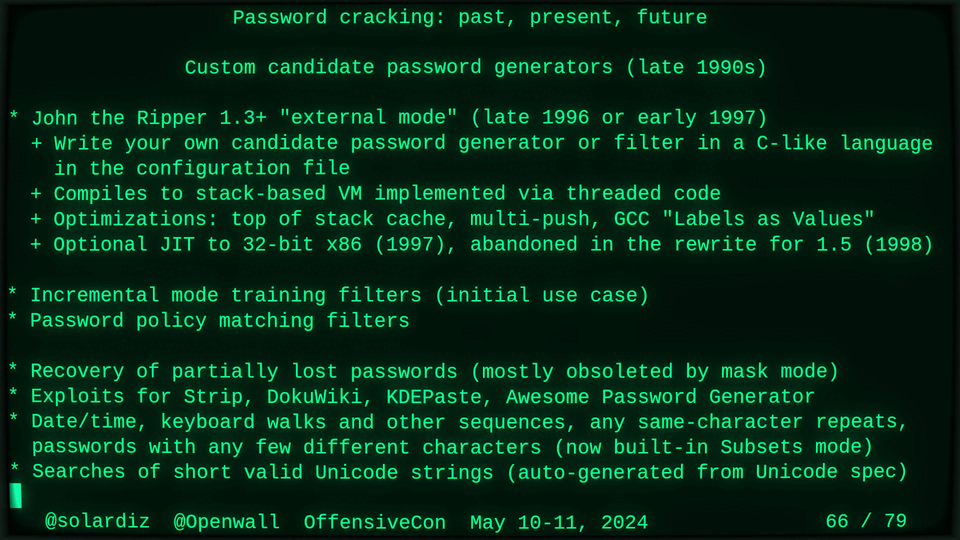
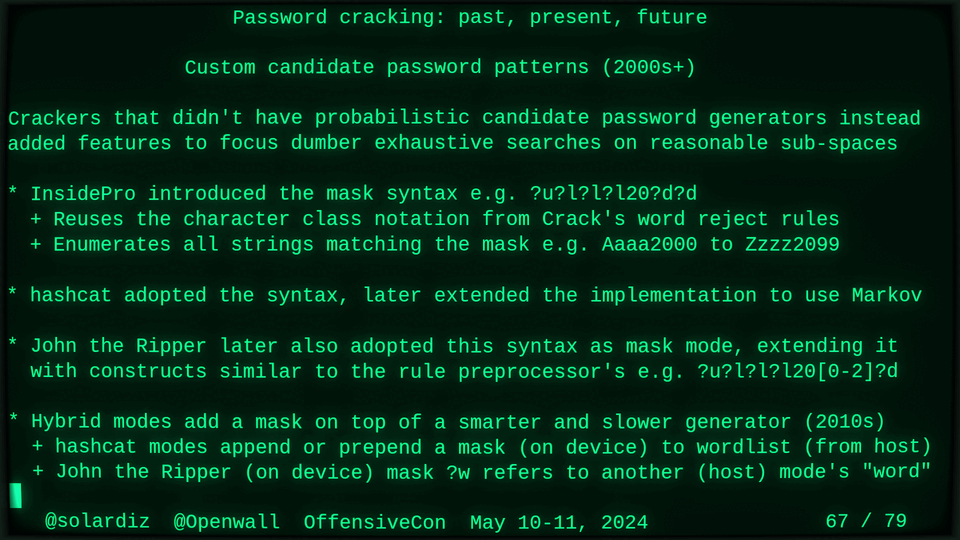
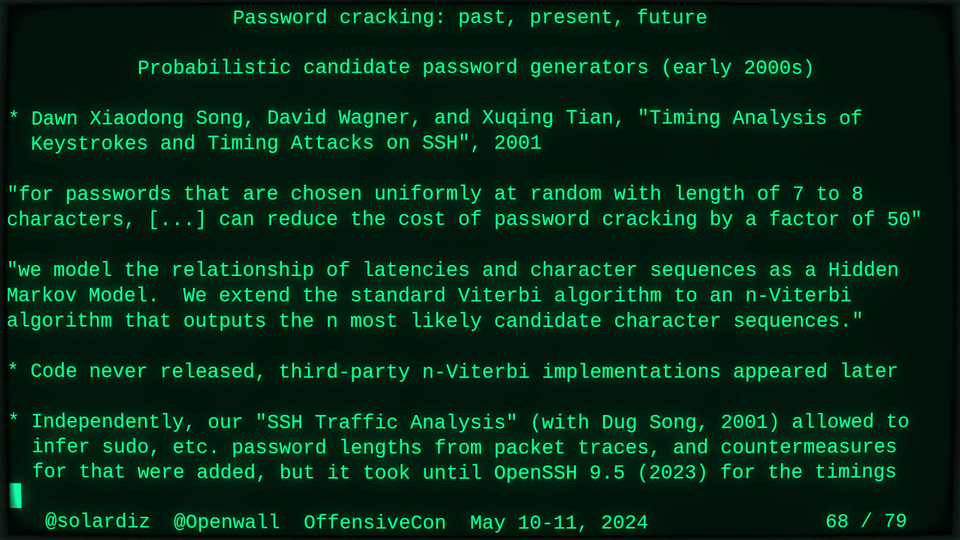
Password cracking: past, present, future
These are the slides of Solar Designer's
keynote talk at OffensiveCon 2024.
You can also watch the
video recording.
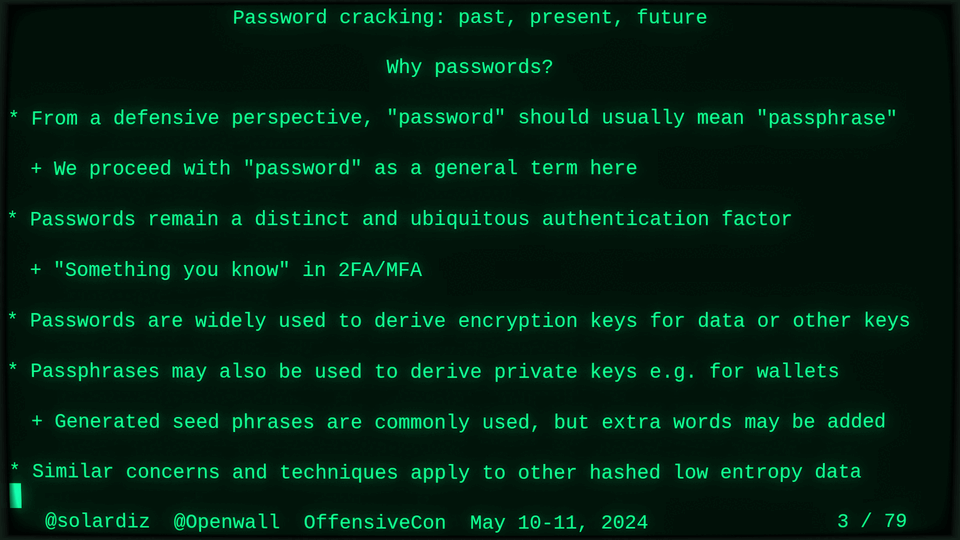
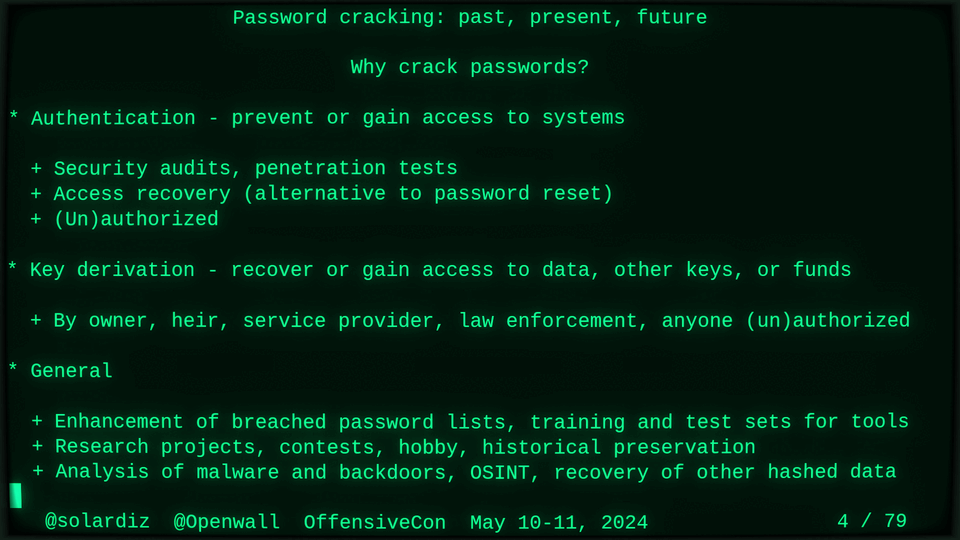
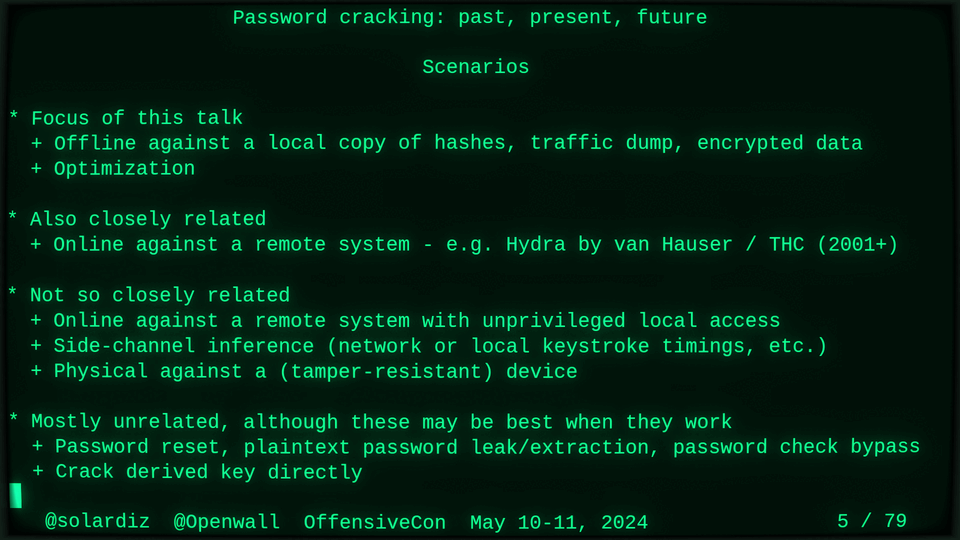
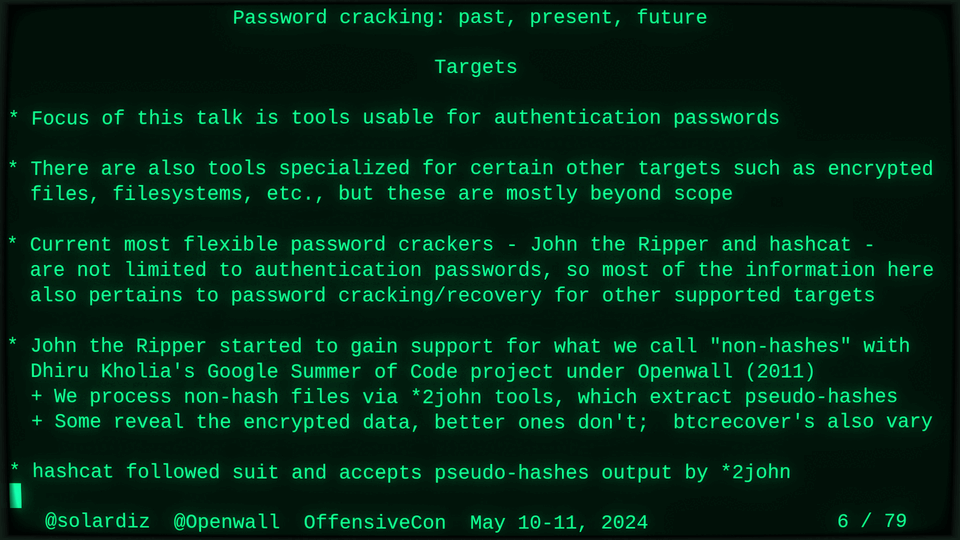
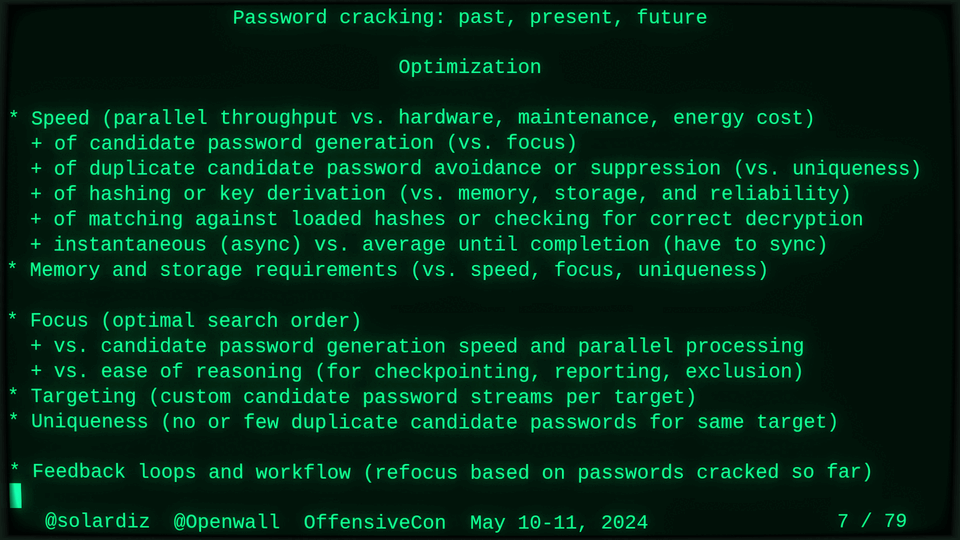
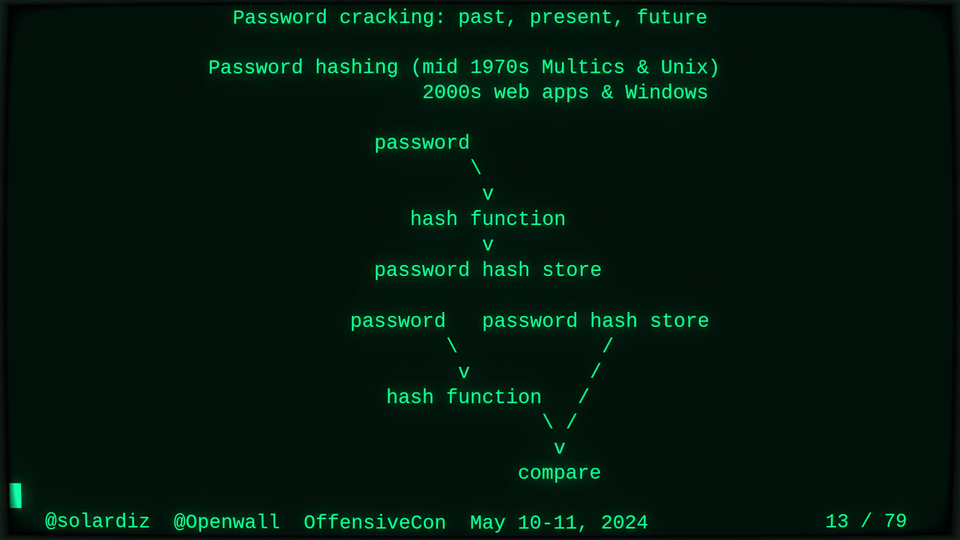
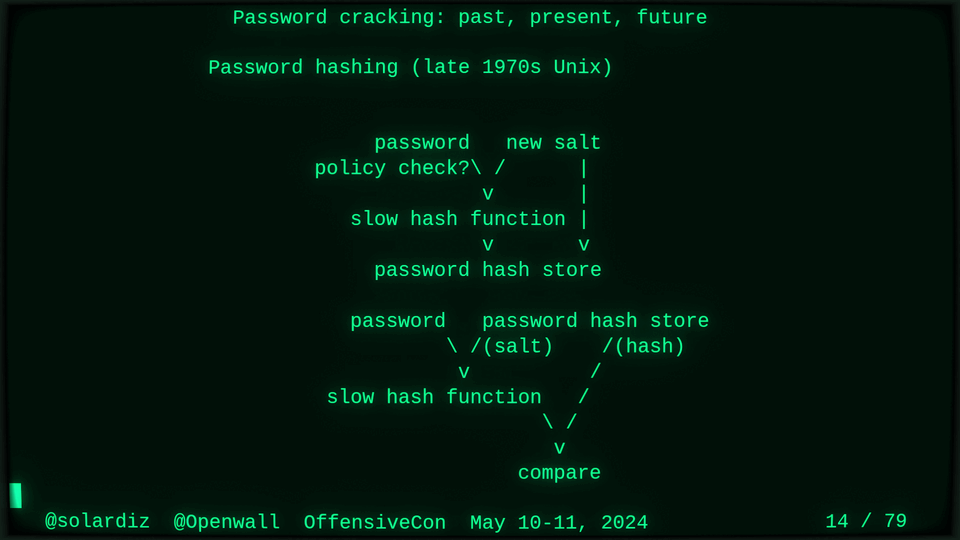
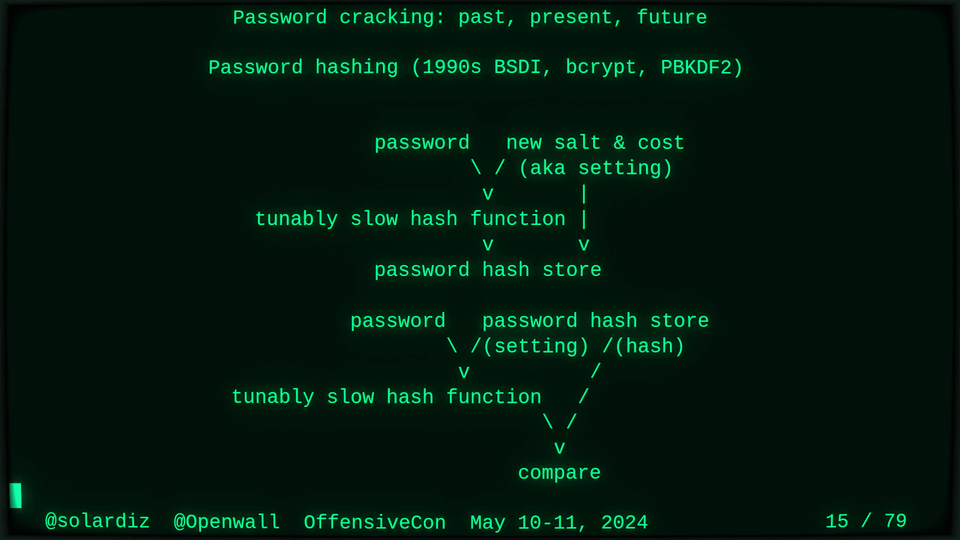
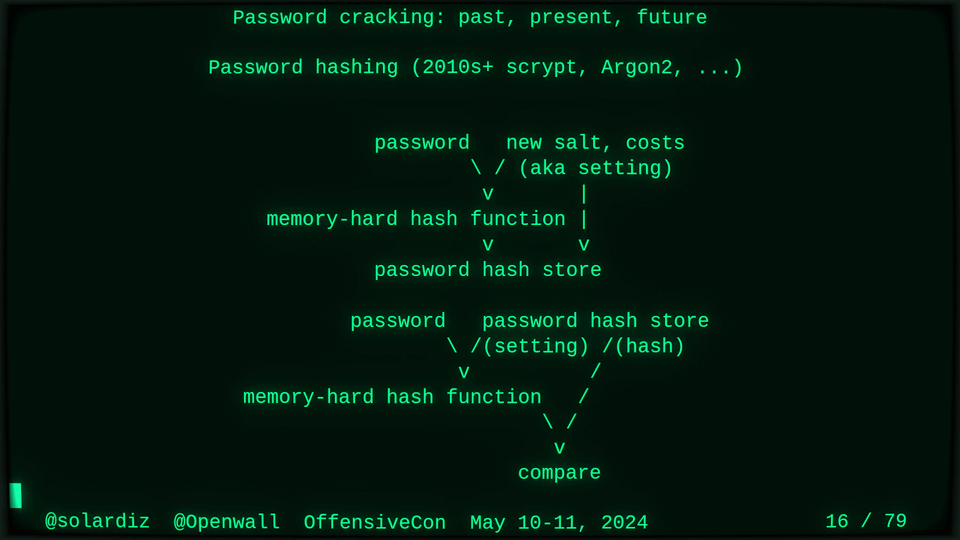
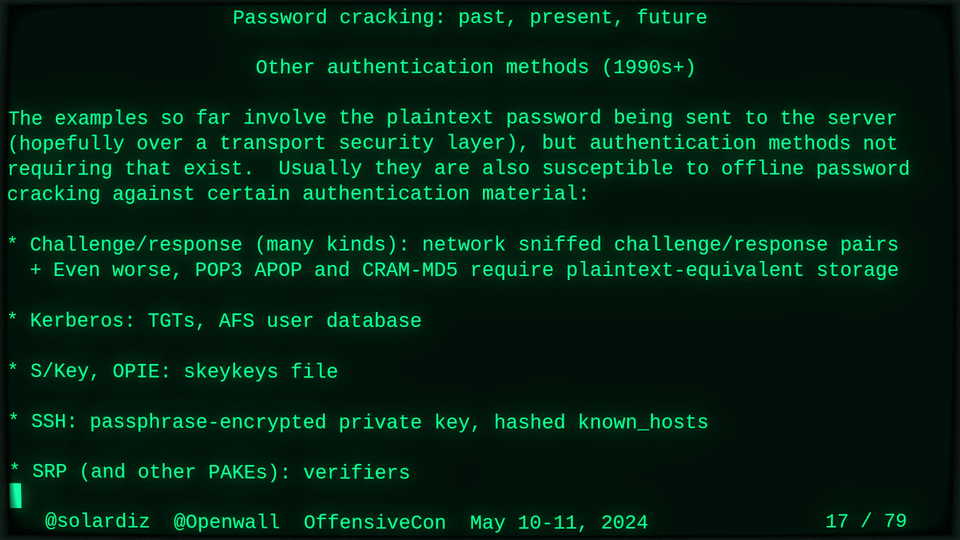
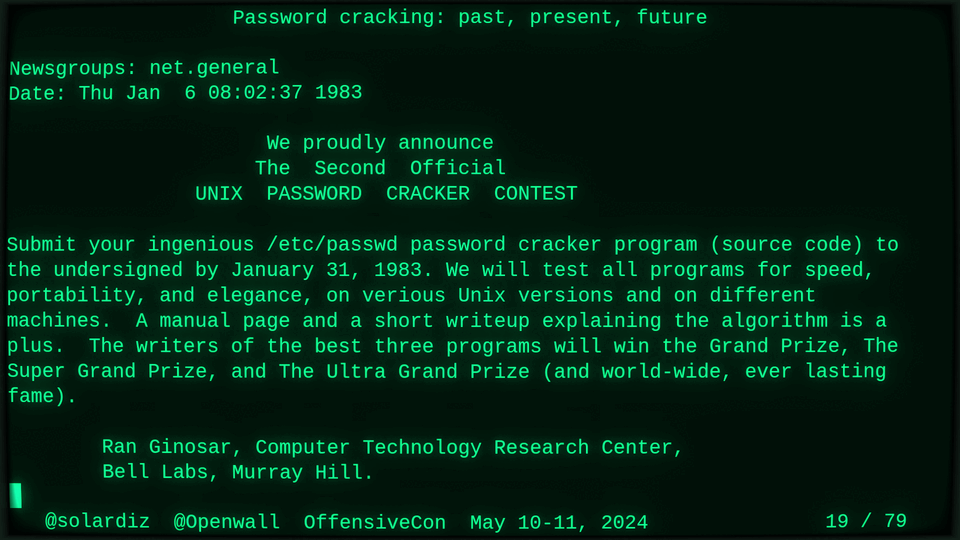
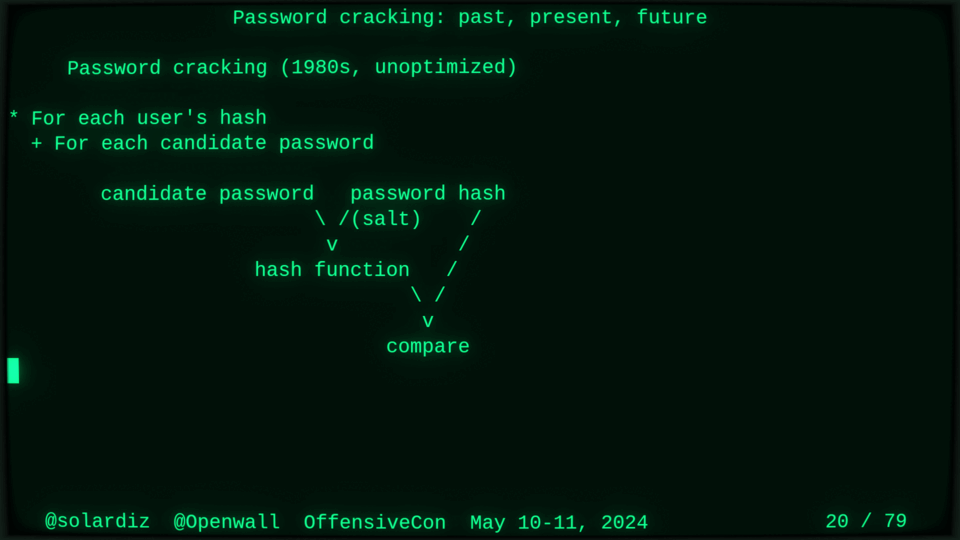
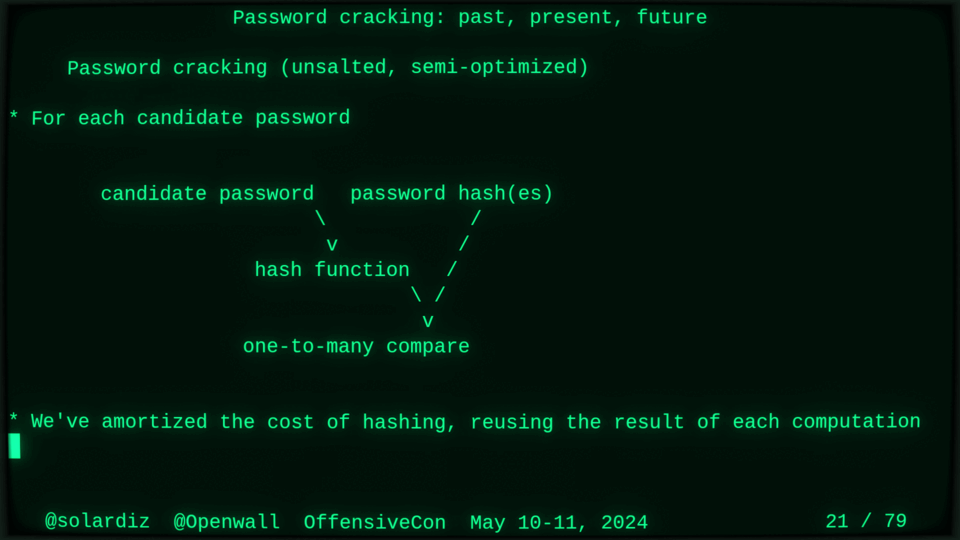
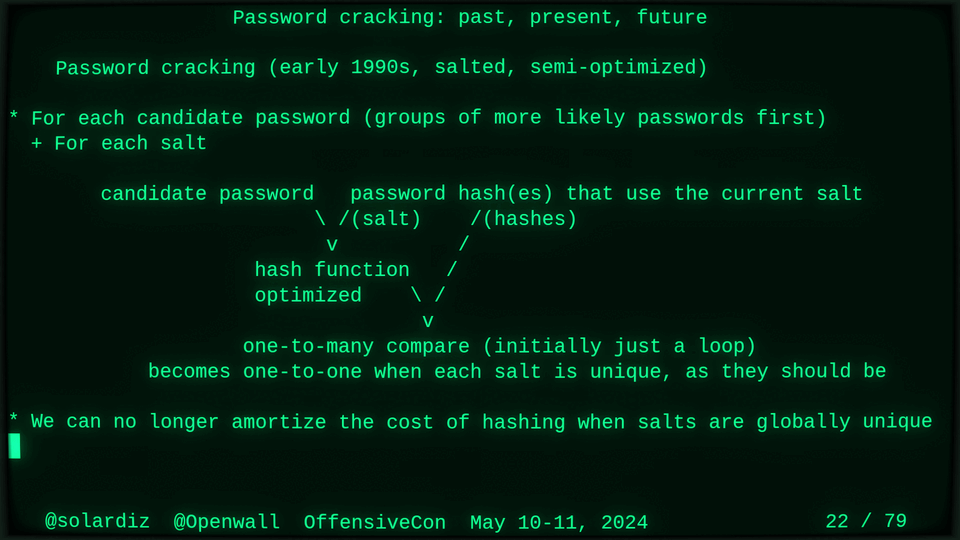
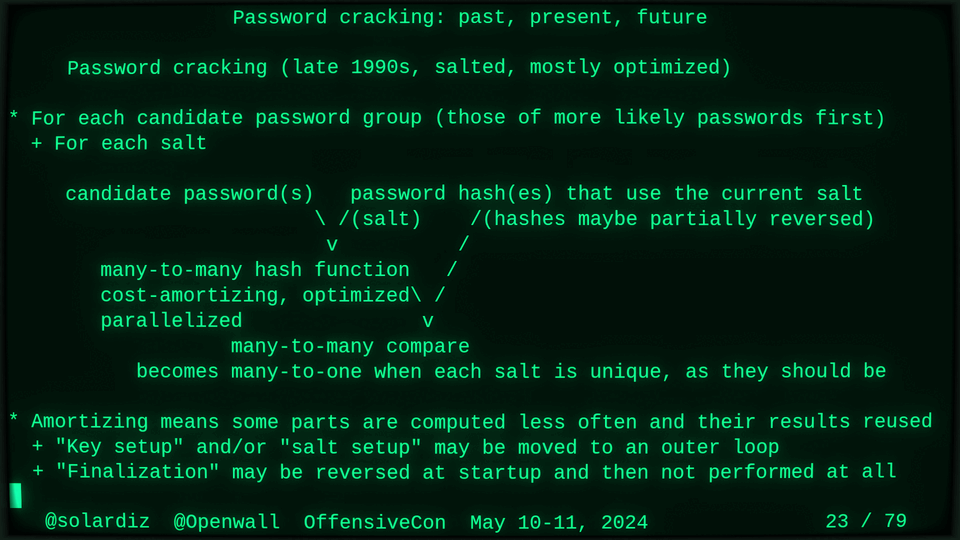
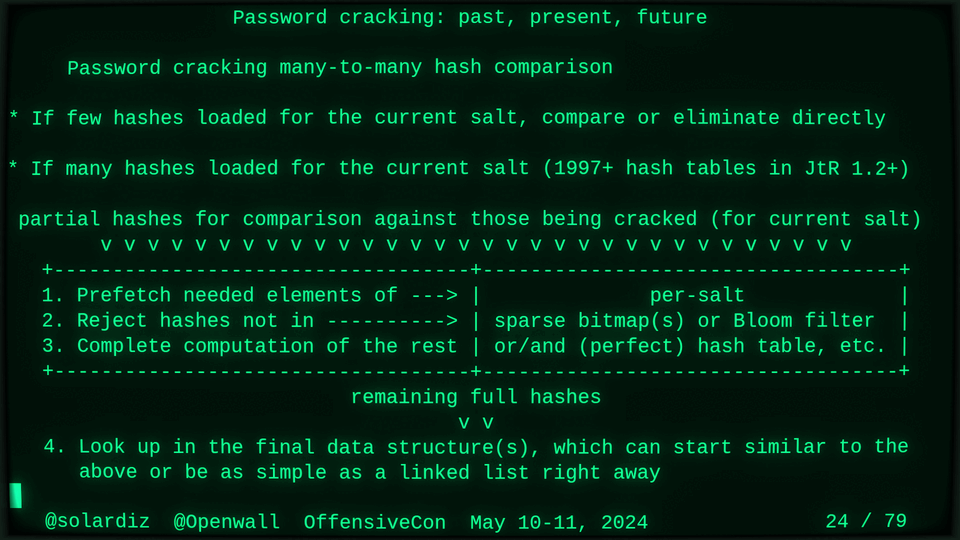
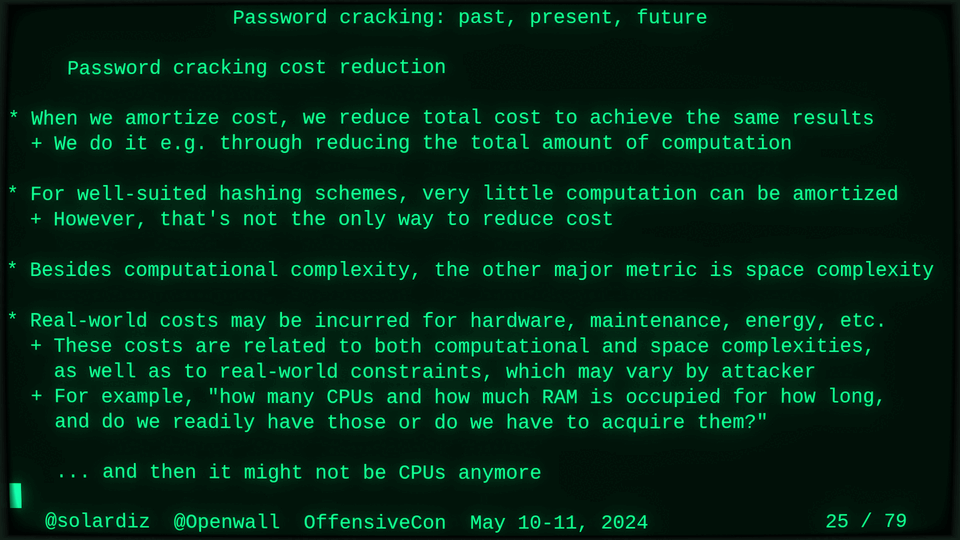
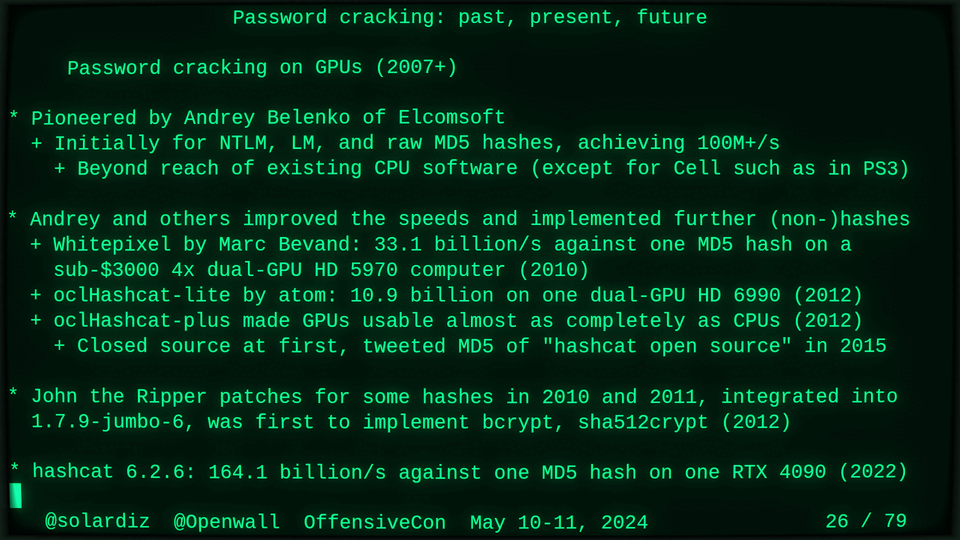
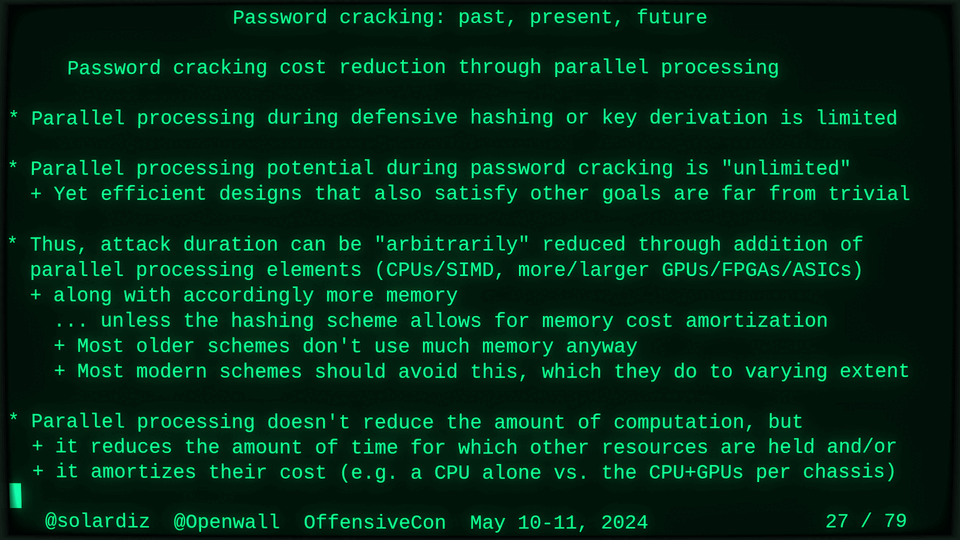
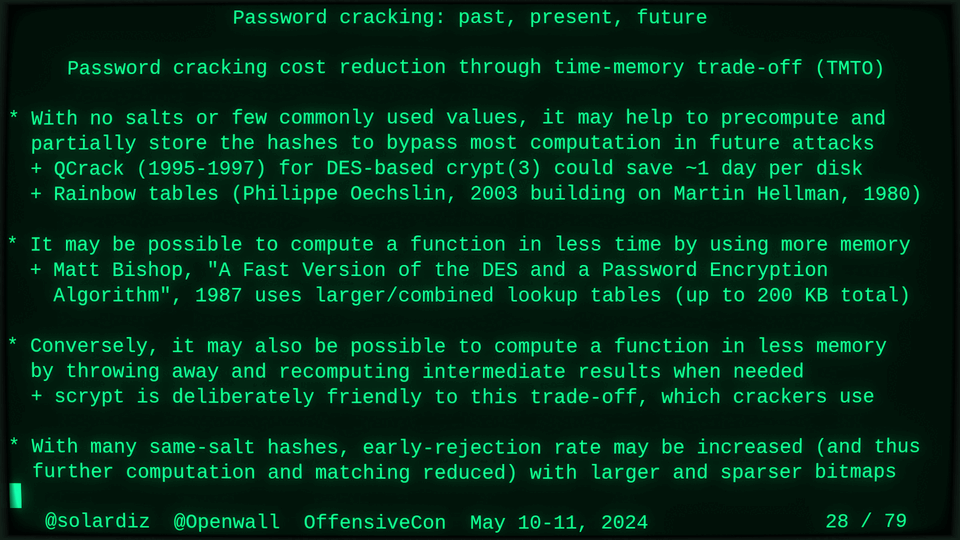
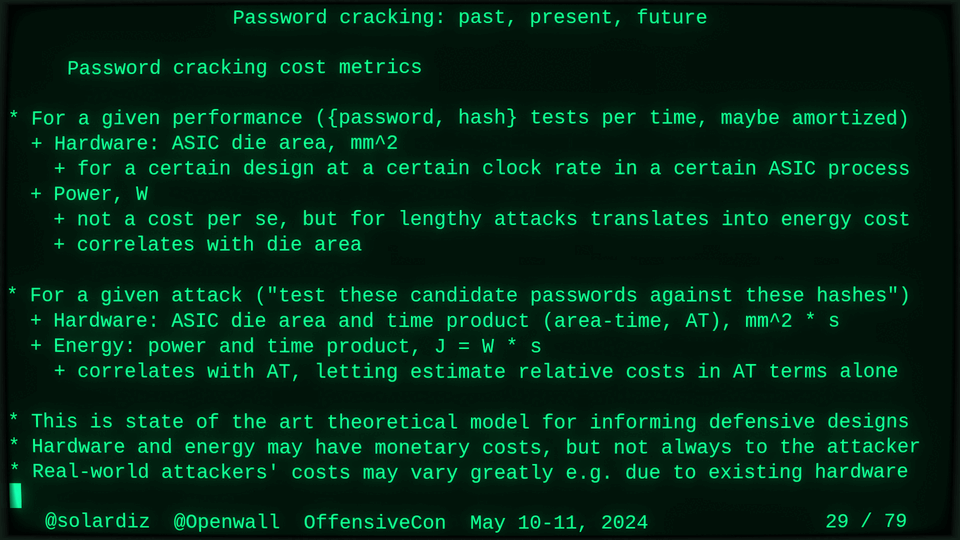
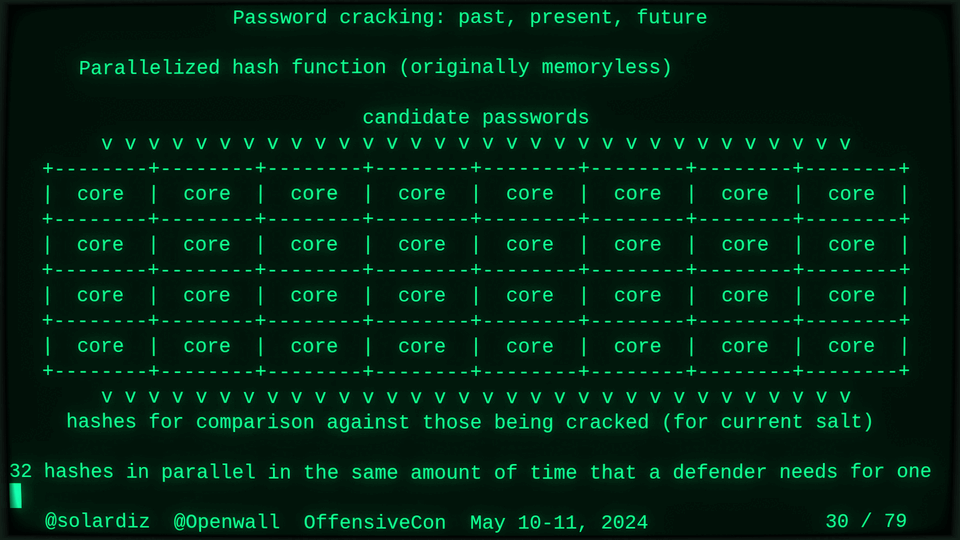
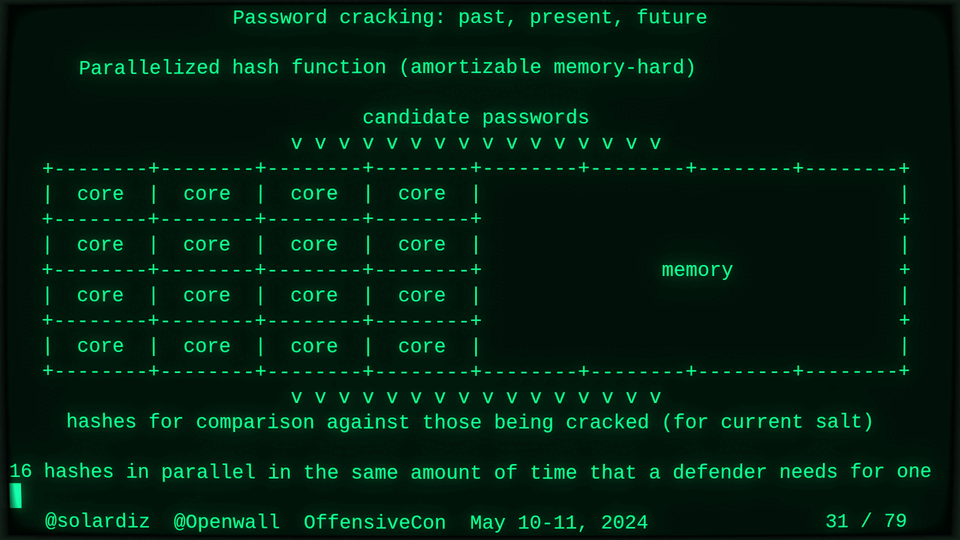
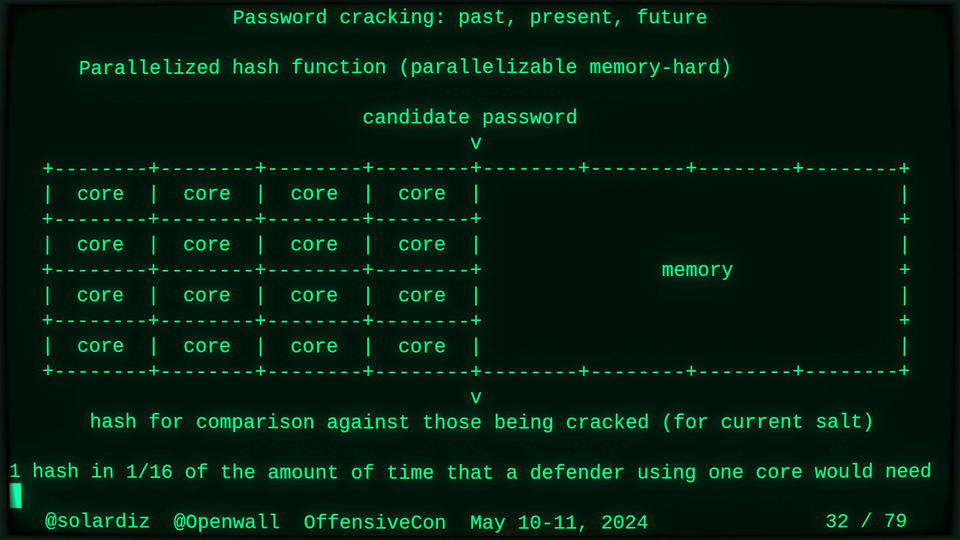
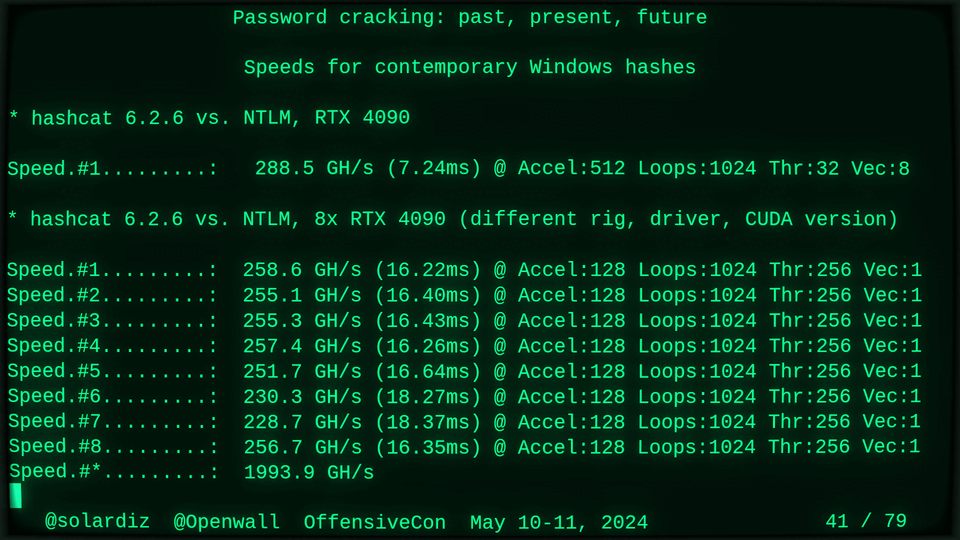
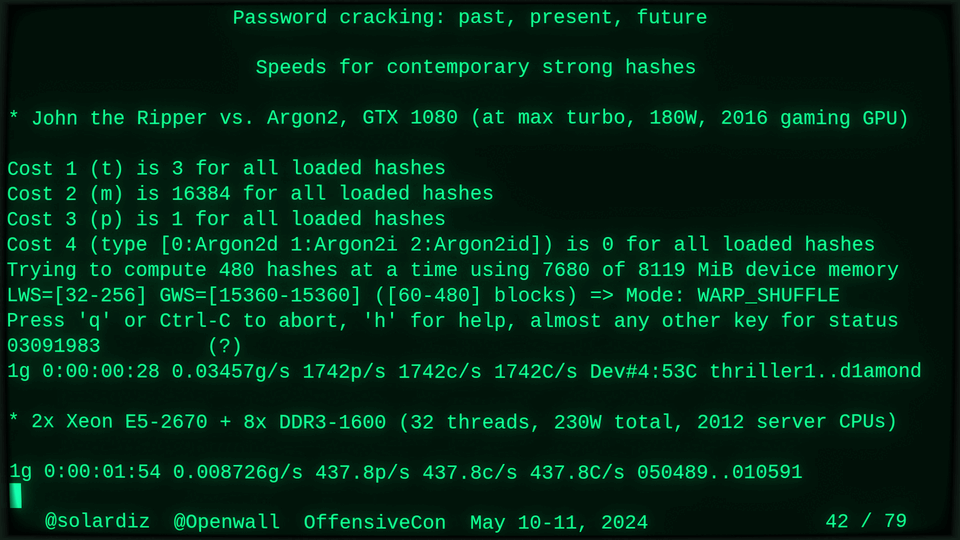
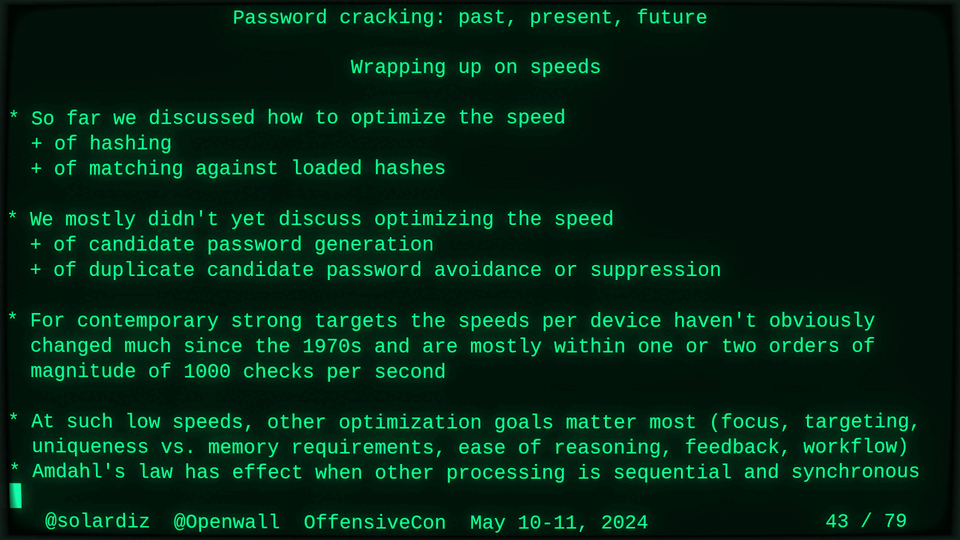
Passwords (or phrases) remain a distinct and ubiquitous authentication factor. They are also widely used to derive encryption keys for data or other keys. Password cracking is used in security audits, penetration testing, to recover or gain access to data, keys, or funds, and for a variety of other purposes. Focus of this talk is evolution and optimization of offline password cracking. At a high level, we break down the optimization problem into that of speed (how many candidate passwords we test per second) and focus (which candidate passwords we test against which targets and in what order). Also included is plenty of historical context starting with 1960s and until the present day, with a look into the future.
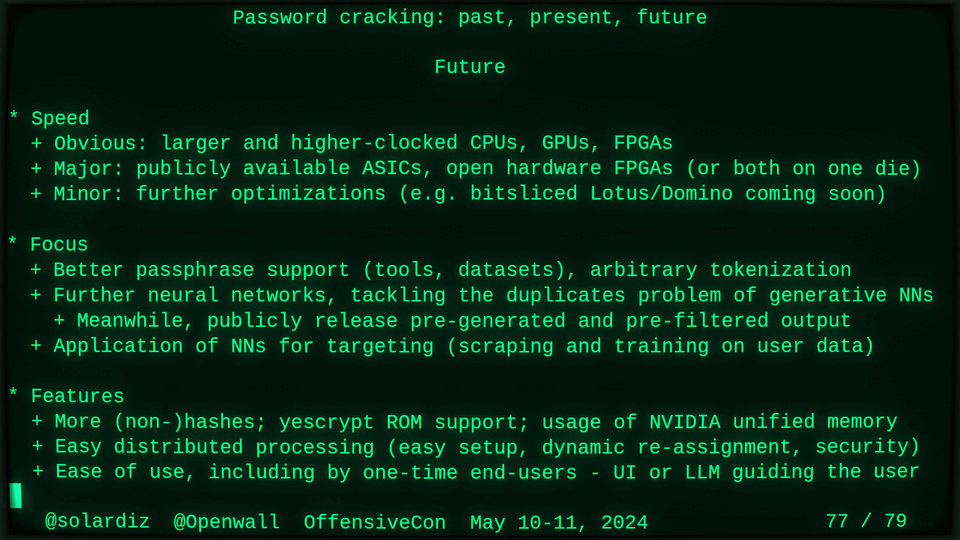
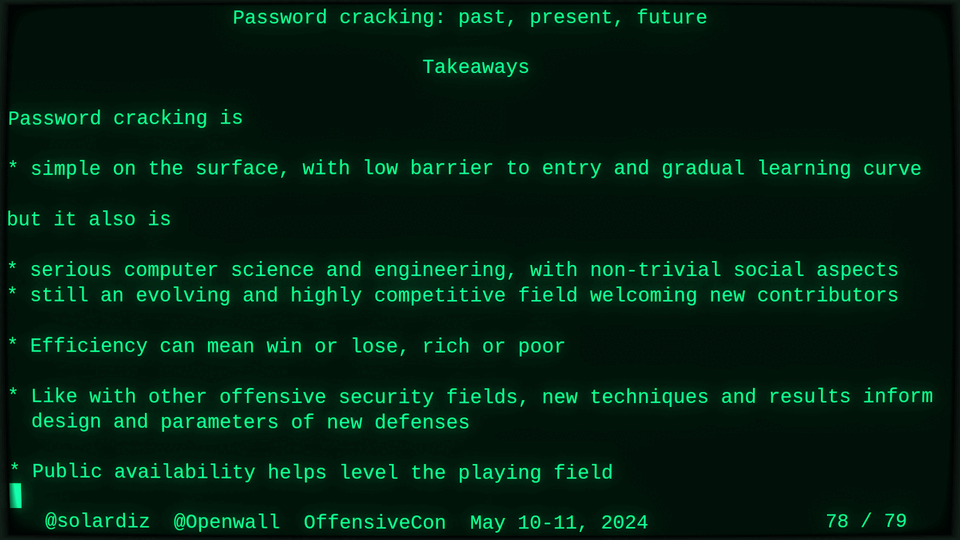
Password cracking may be simple on the surface, but it is also serious computer science and engineering and is still an evolving and highly competitive field welcoming new contributors. Like with other offensive security fields, new techniques and results inform design and parameters of new defenses.
In a sense, this presentation is the offensive security counterpart to our earlier
Password security: past, present, future (2012) and
yescrypt: large-scale password hashing (2017).
Also relevant are our
Energy-efficient bcrypt cracking (2014),
Automatic wordlists mangling rules generation (2012),
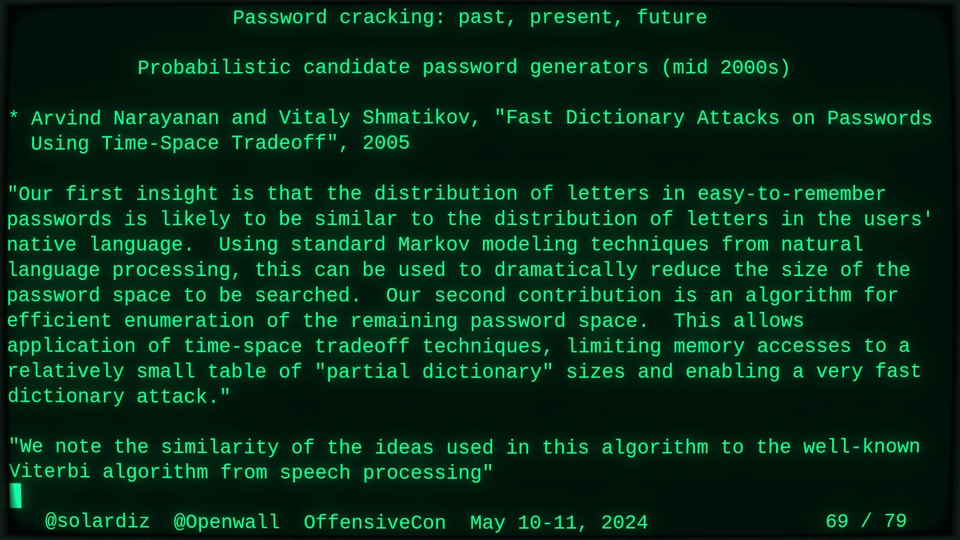
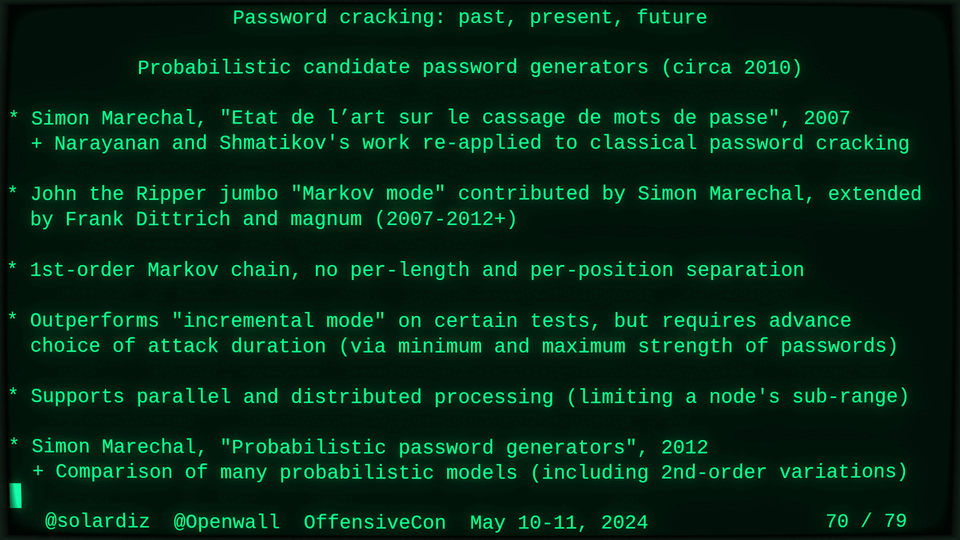
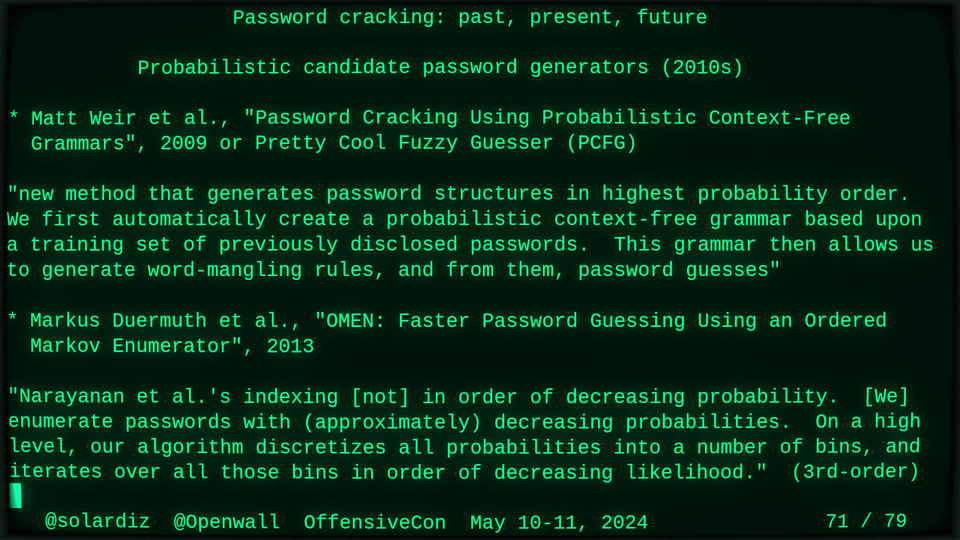
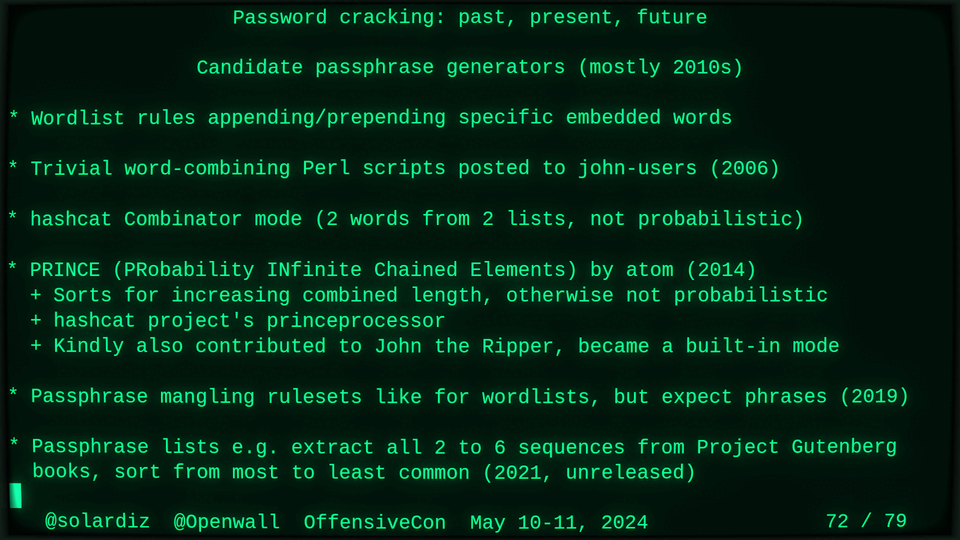
Distributable probabilistic candidate password generators (2012),
and several other presentations.
Please click on the slides for higher-resolution versions.
You can also
download a PDF file with all of the slides (34 MB) or
view them on Speaker Deck.
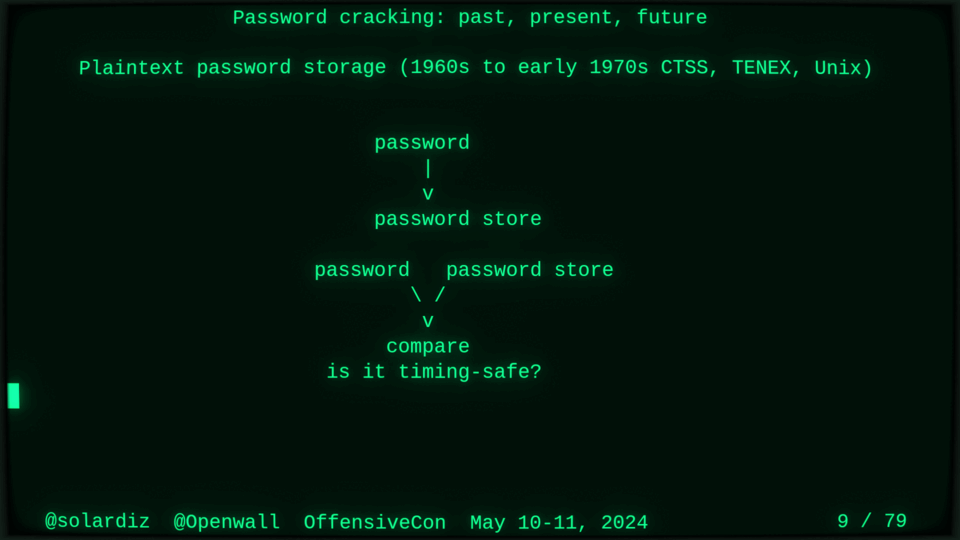
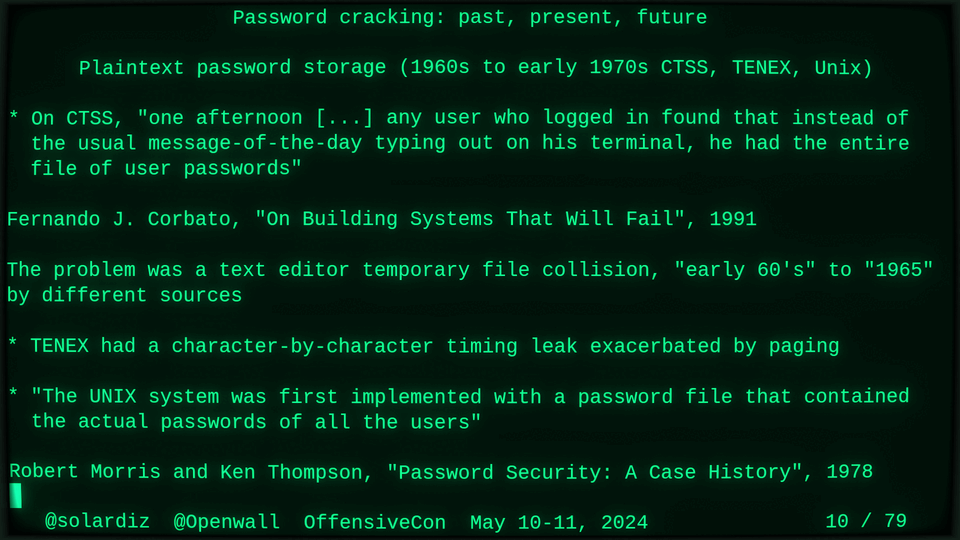
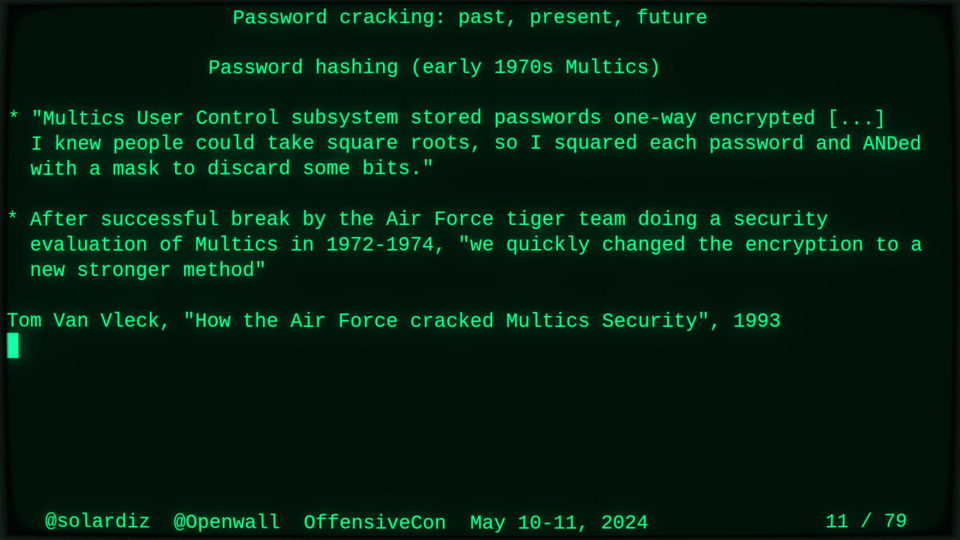
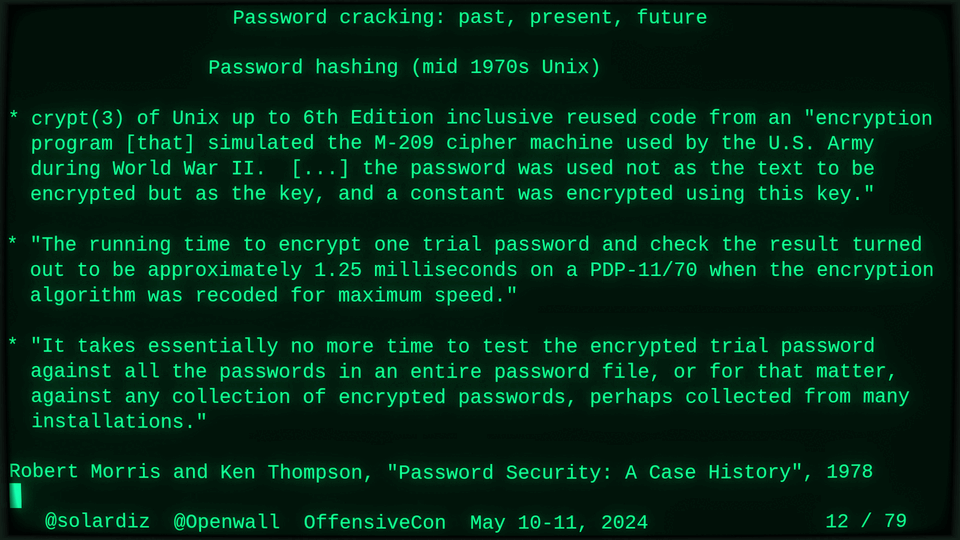
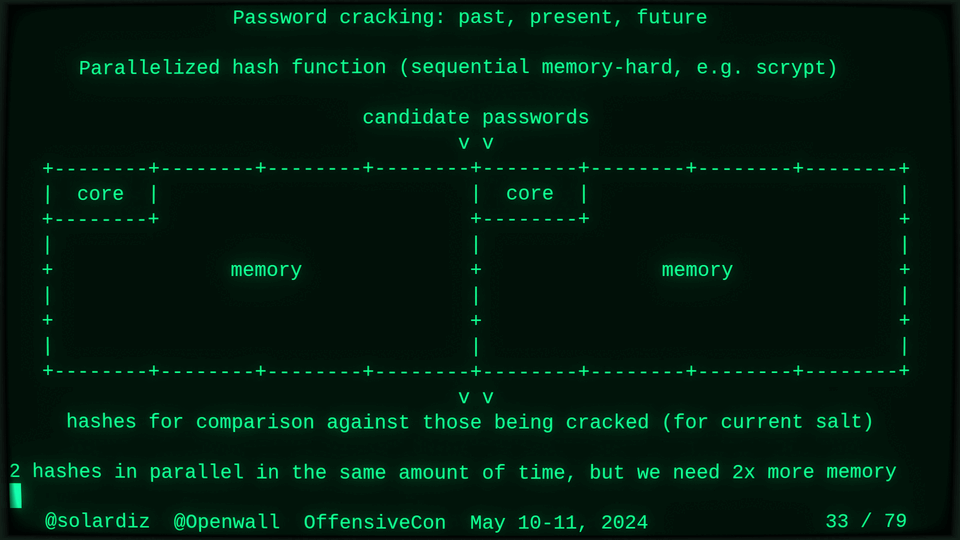
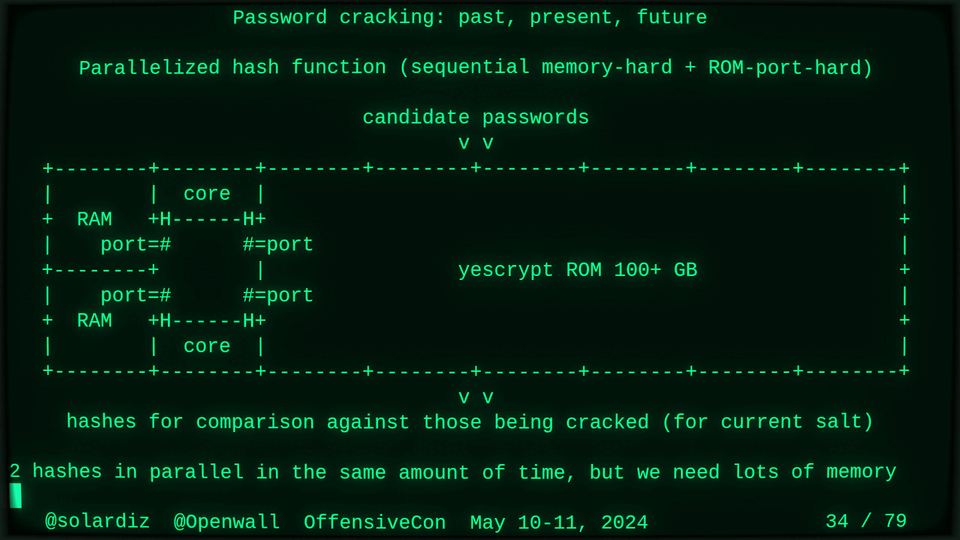
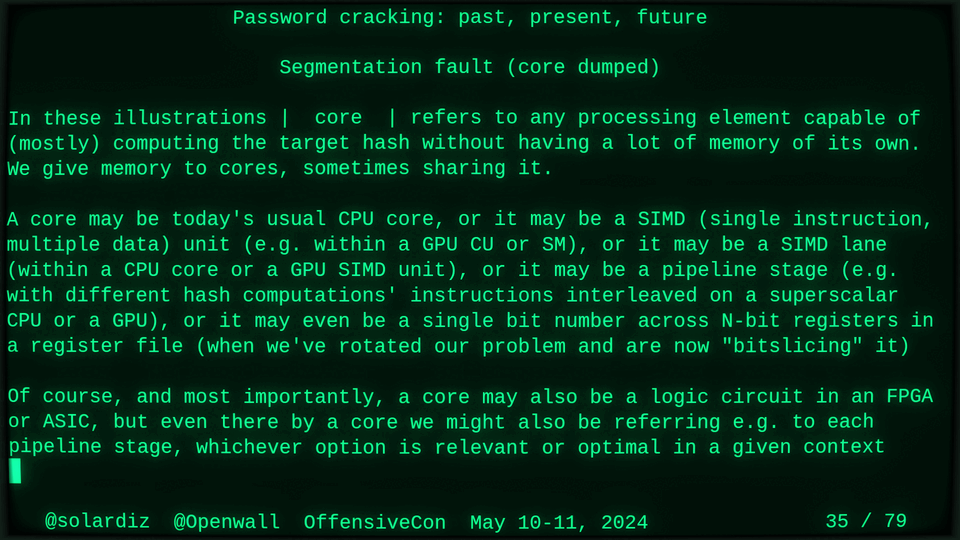
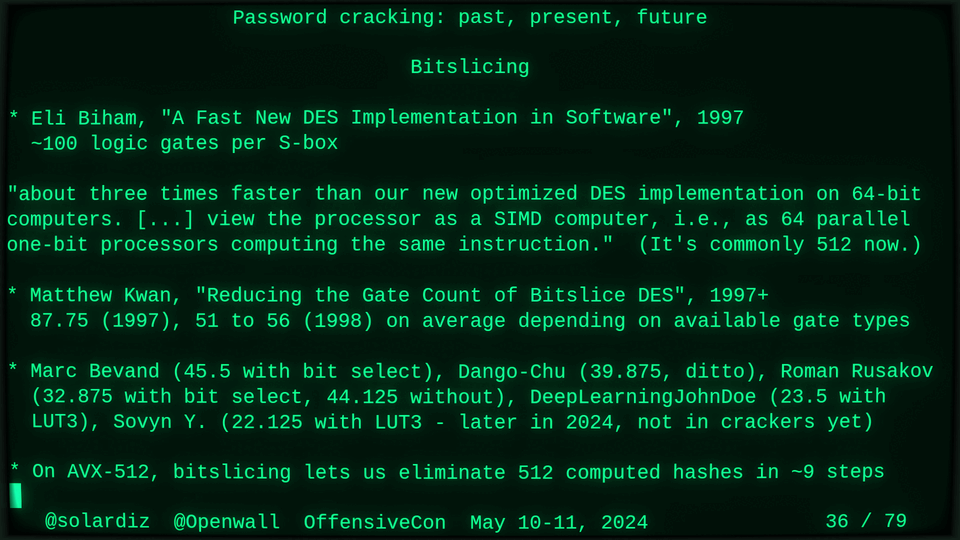
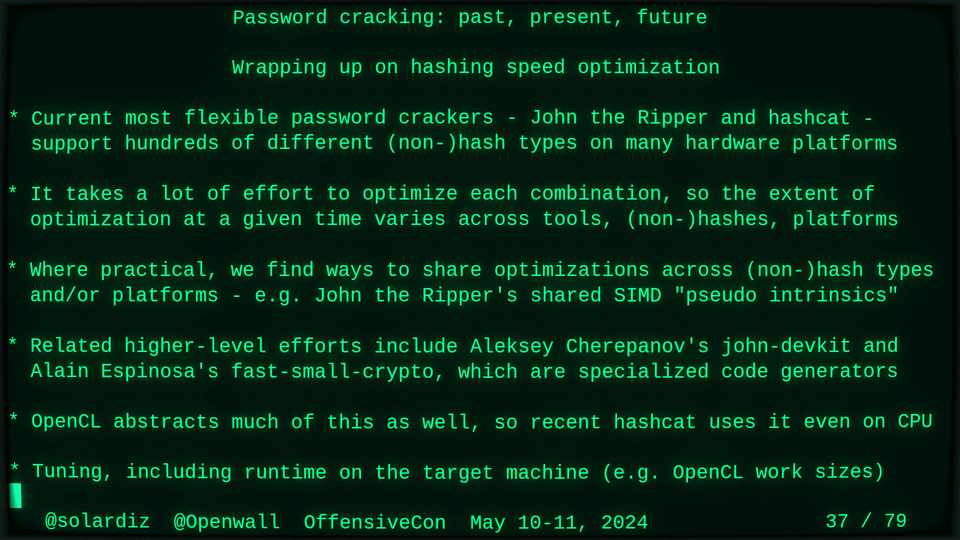
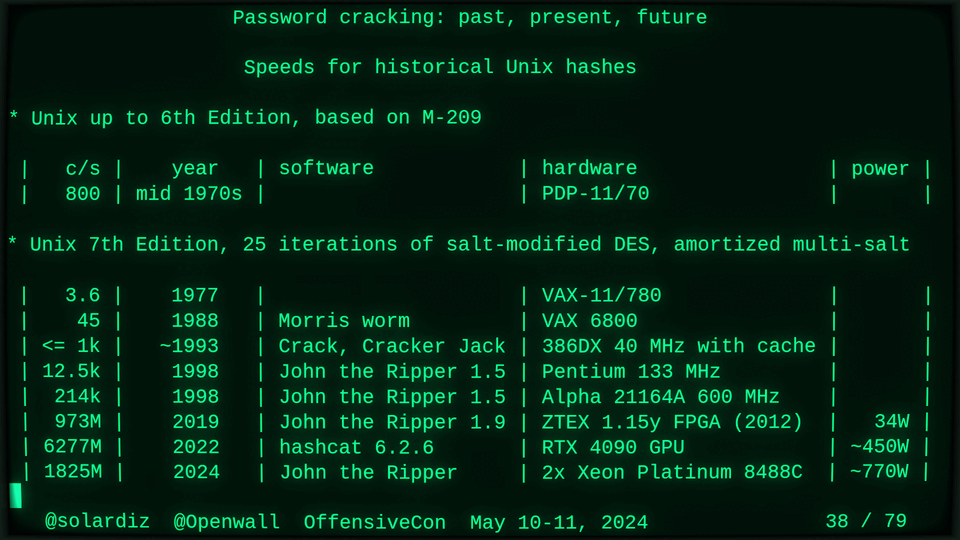
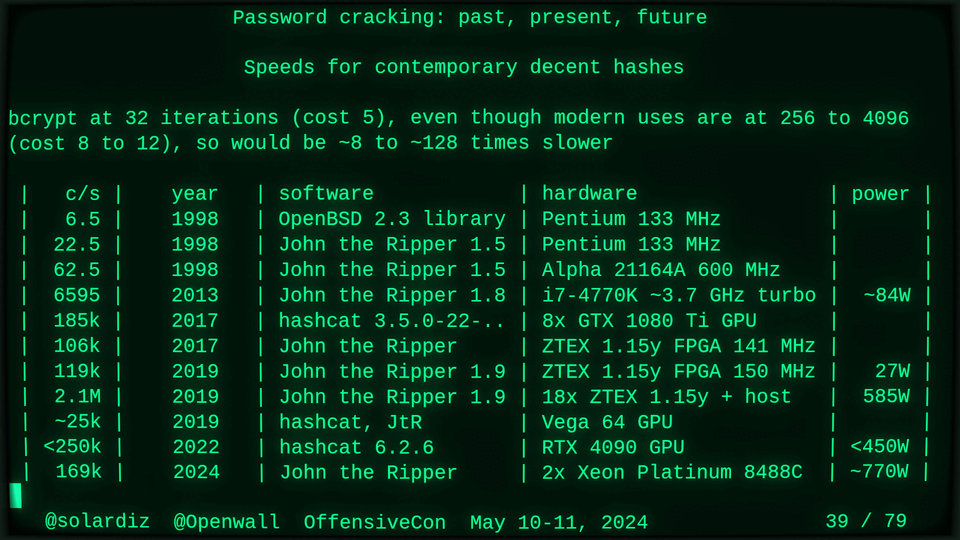
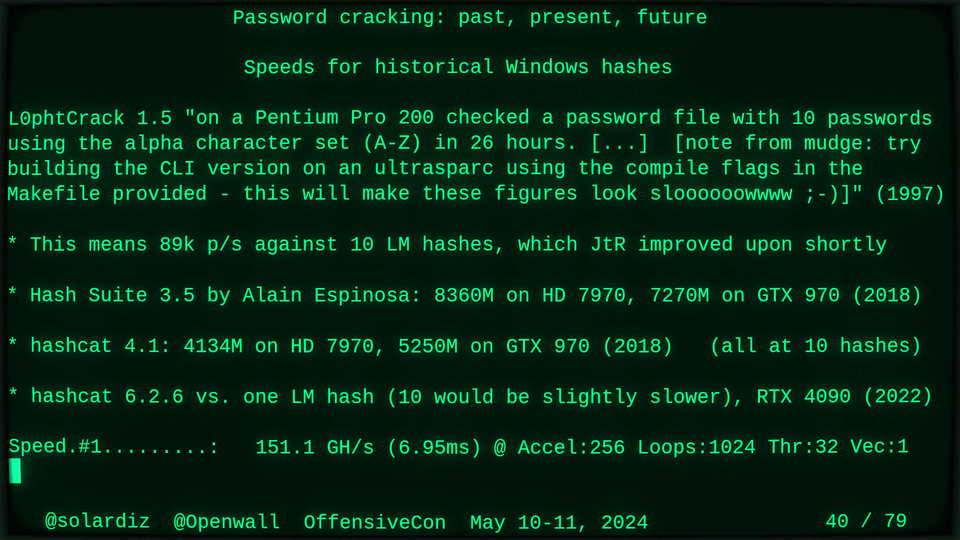
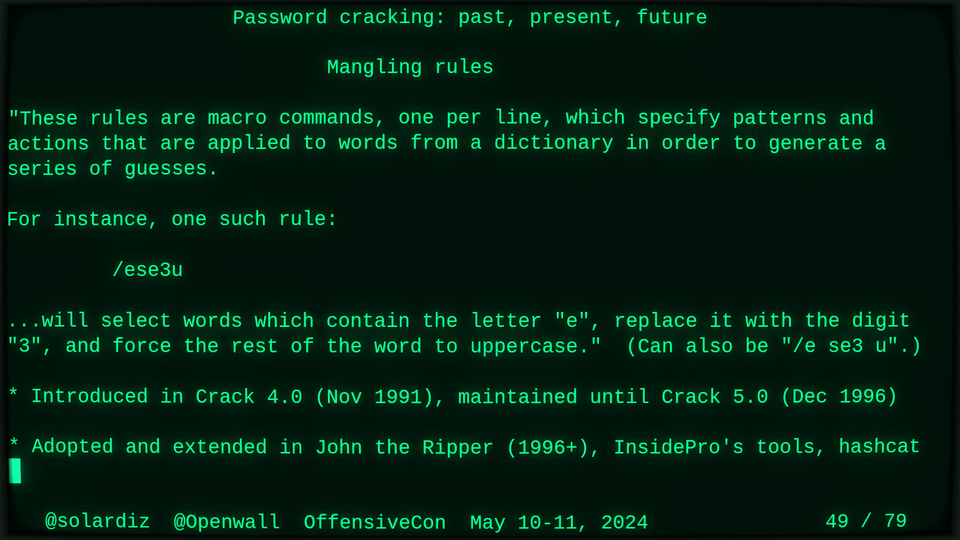
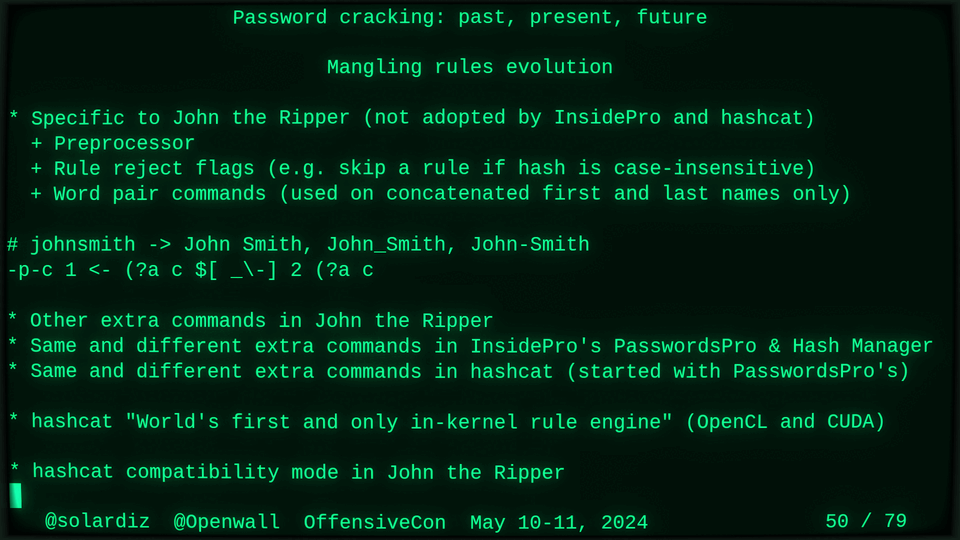
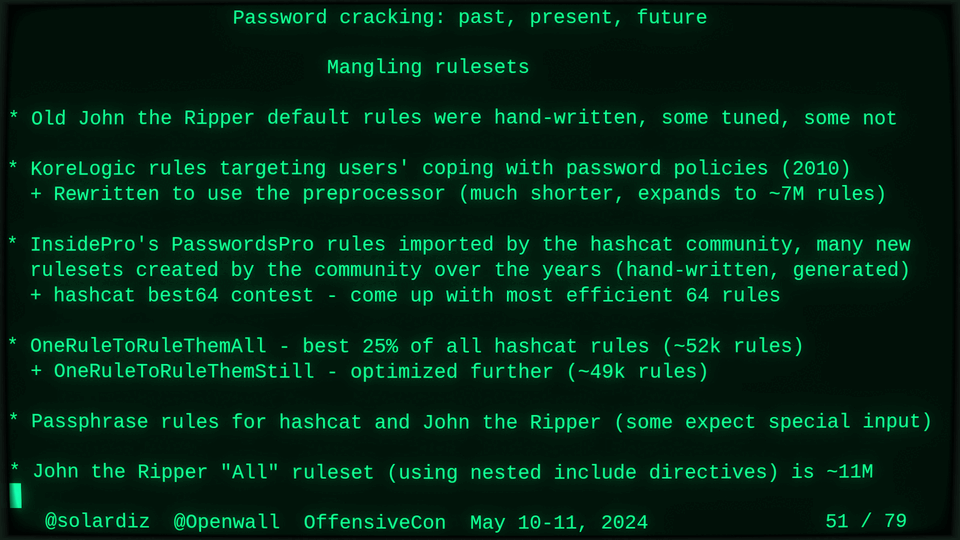
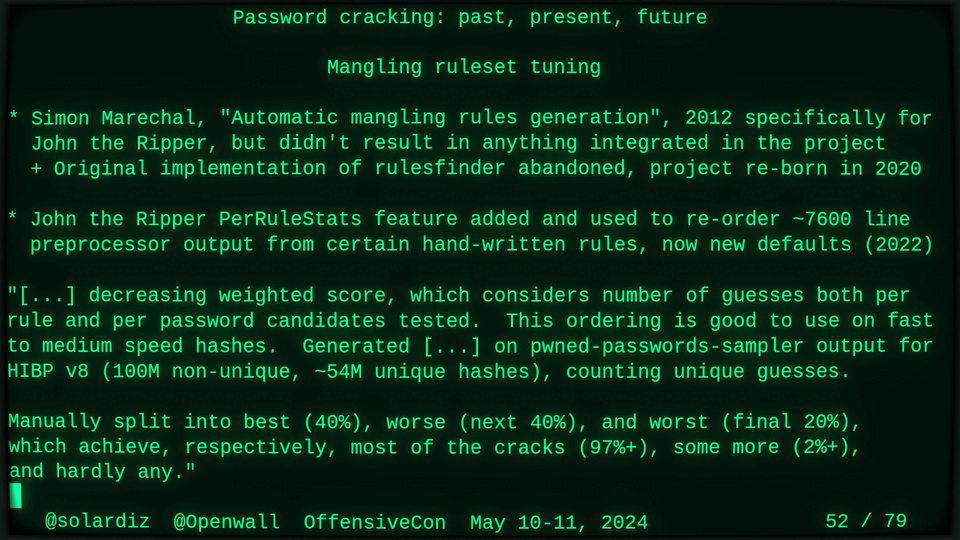
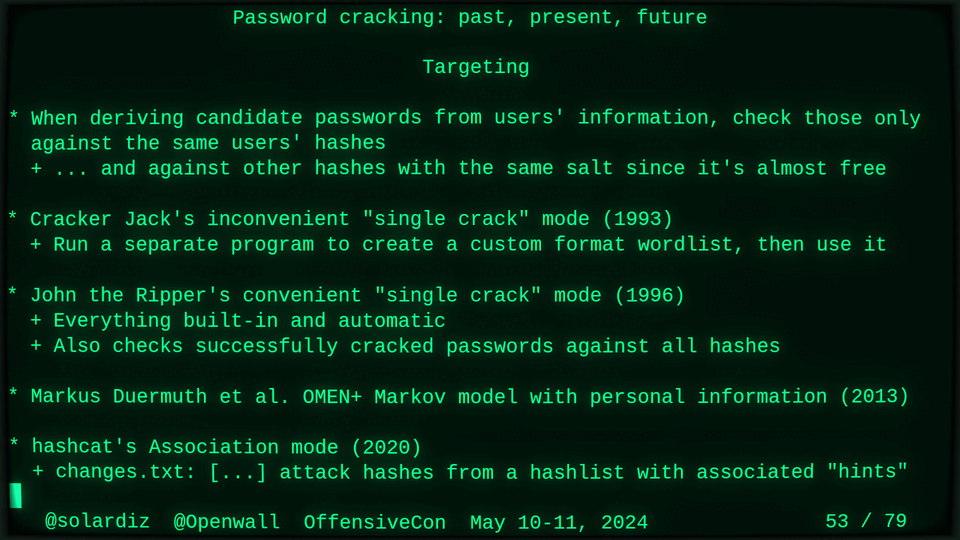
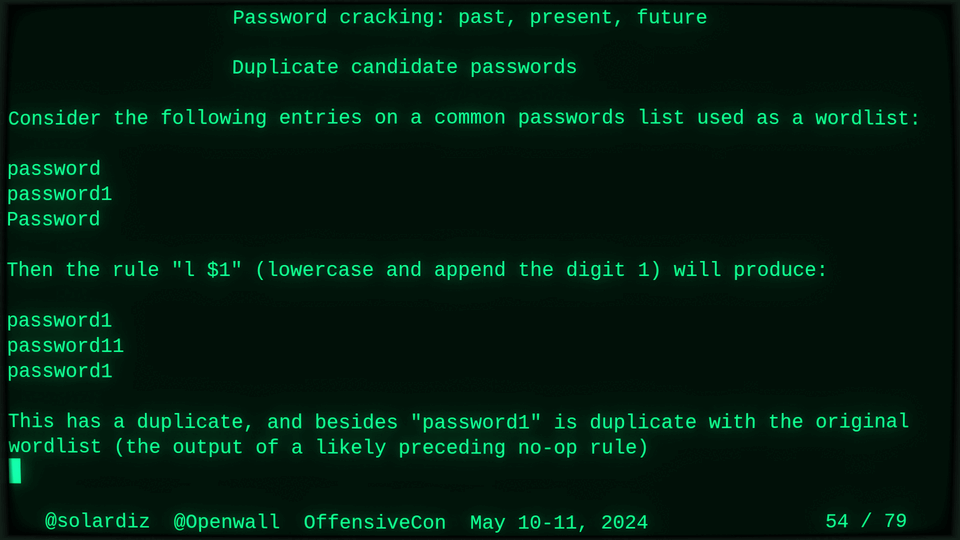
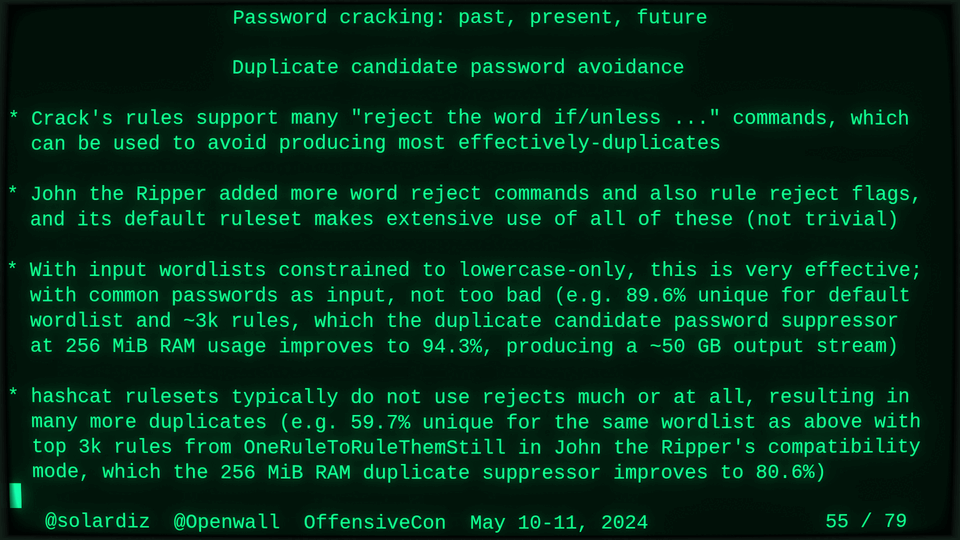
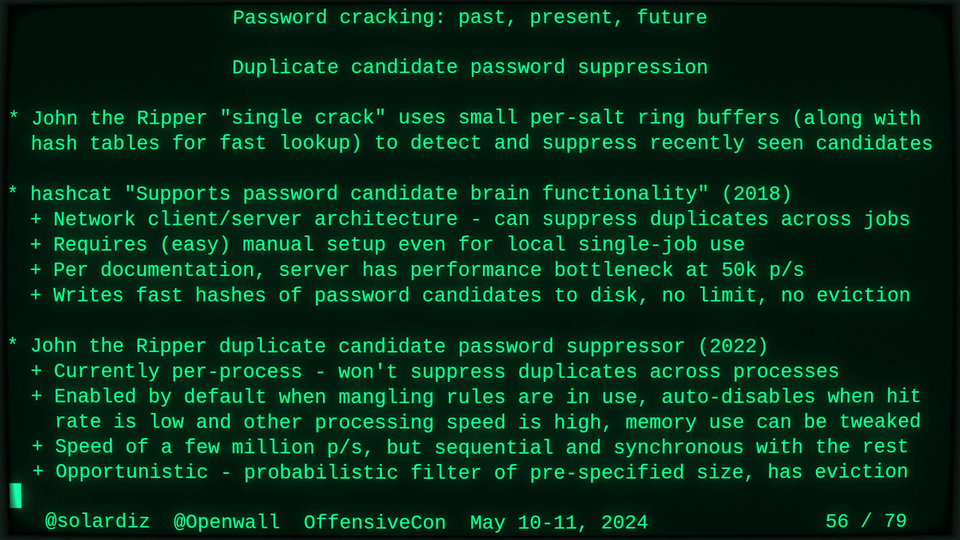
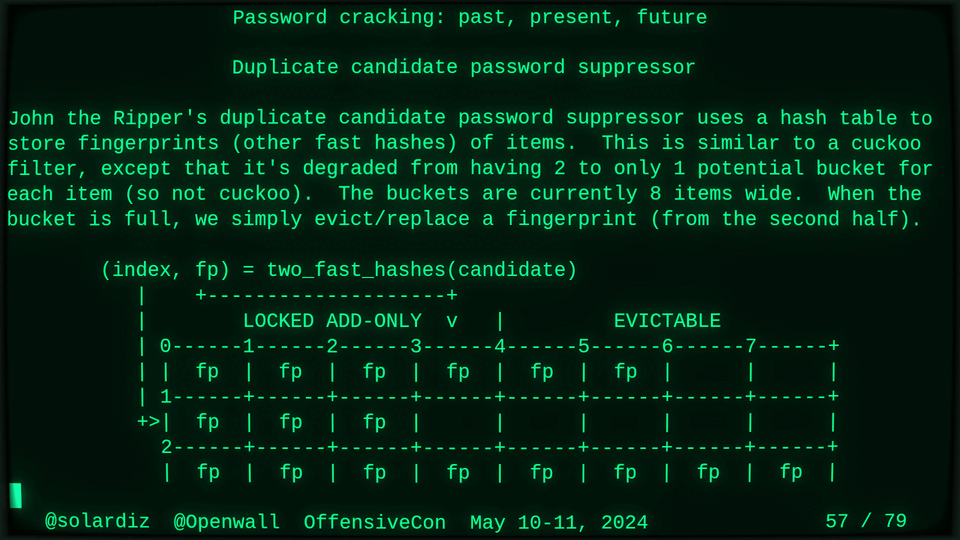
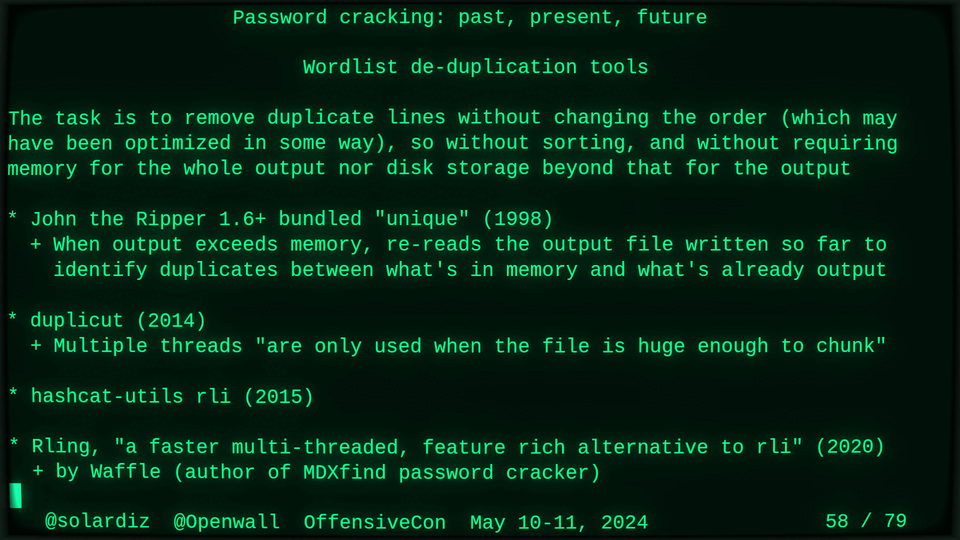
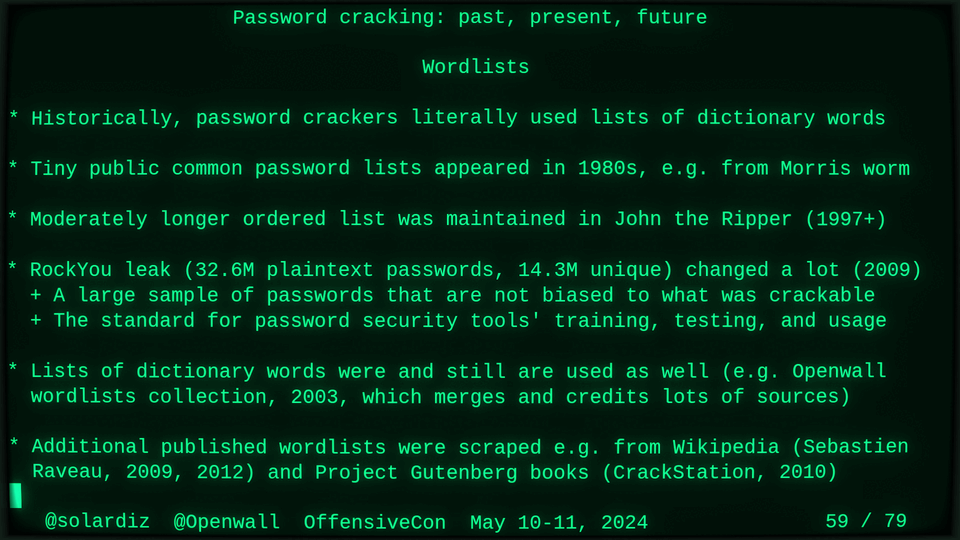
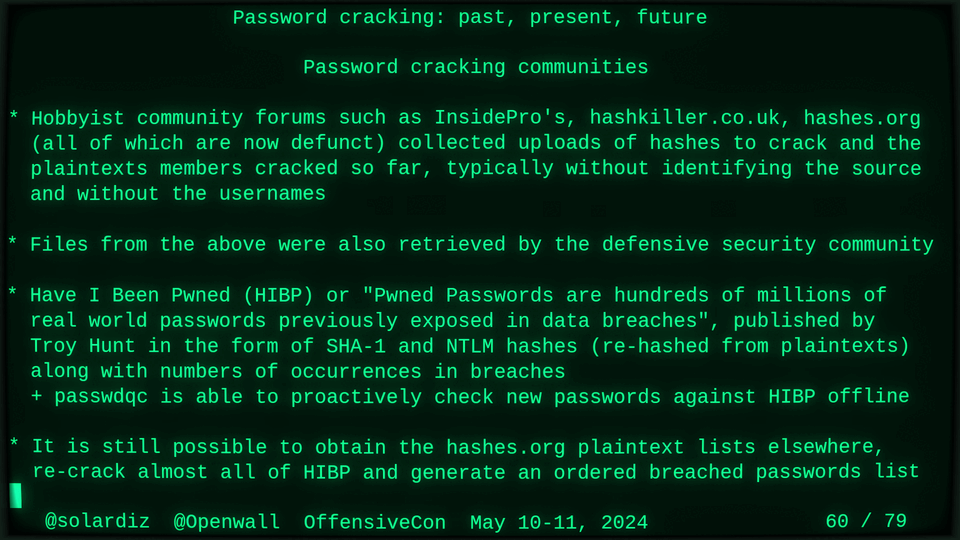
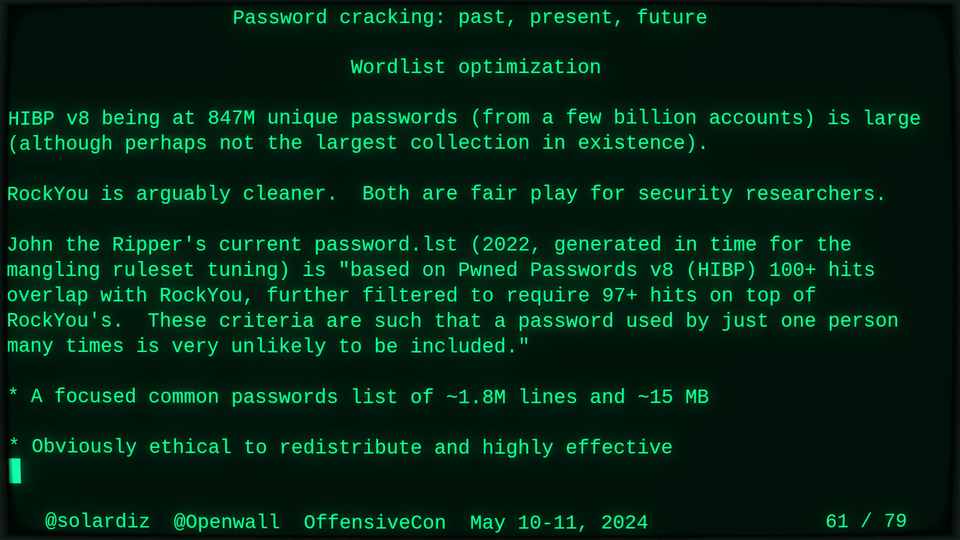
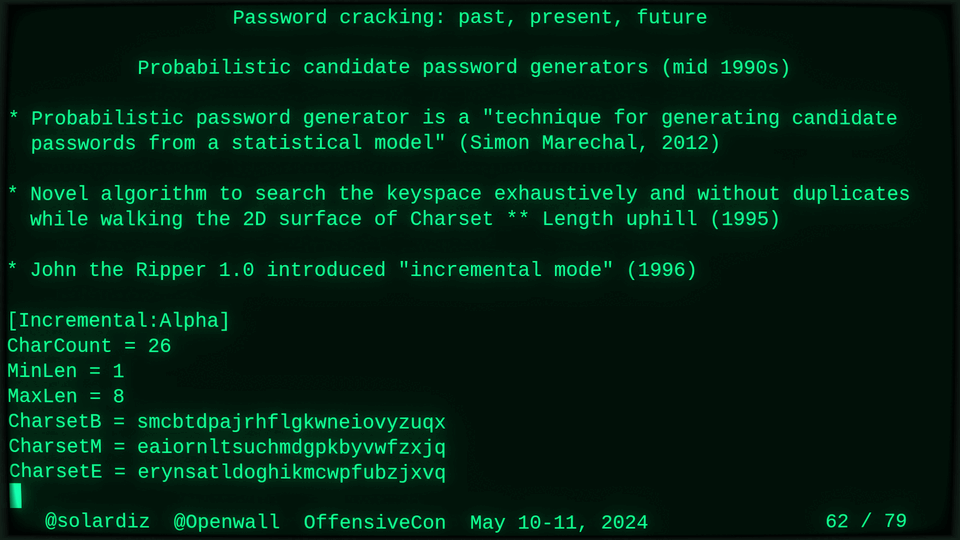
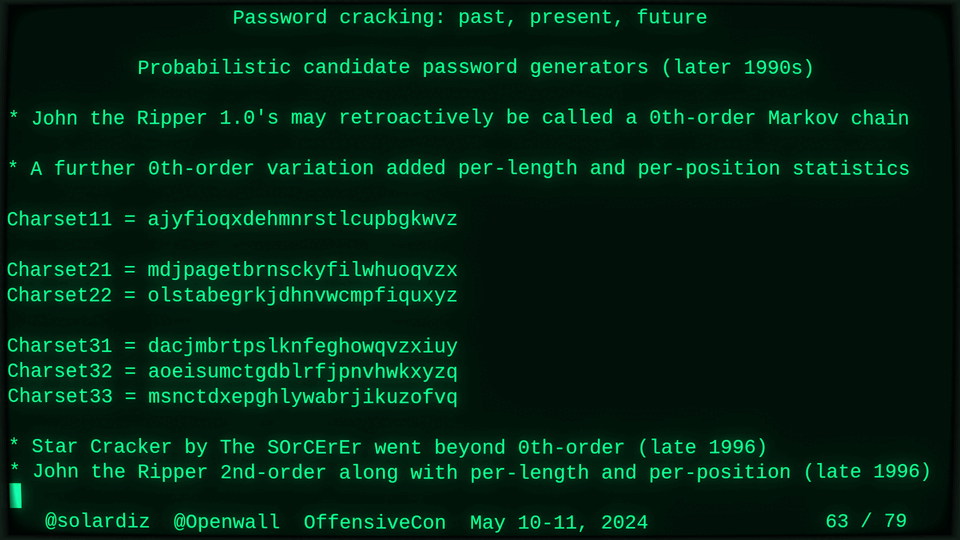
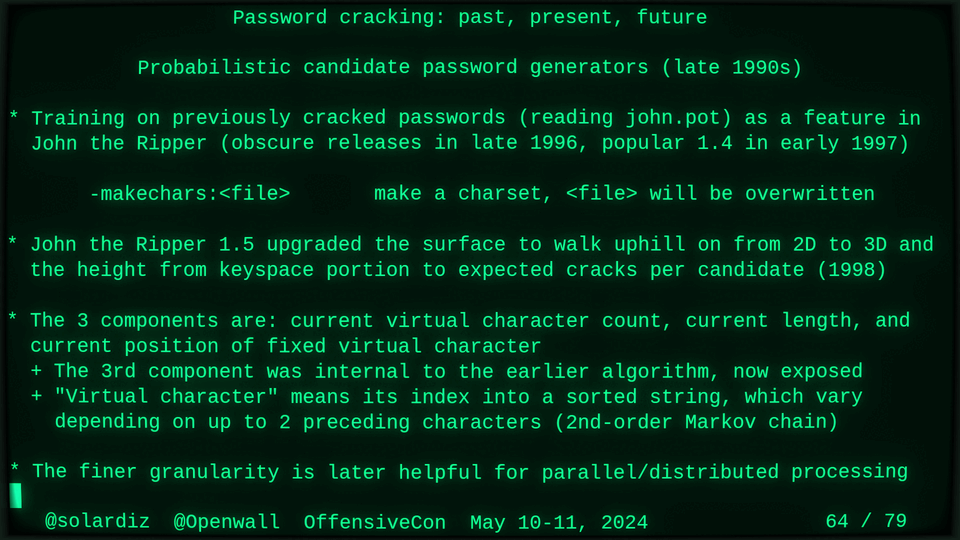
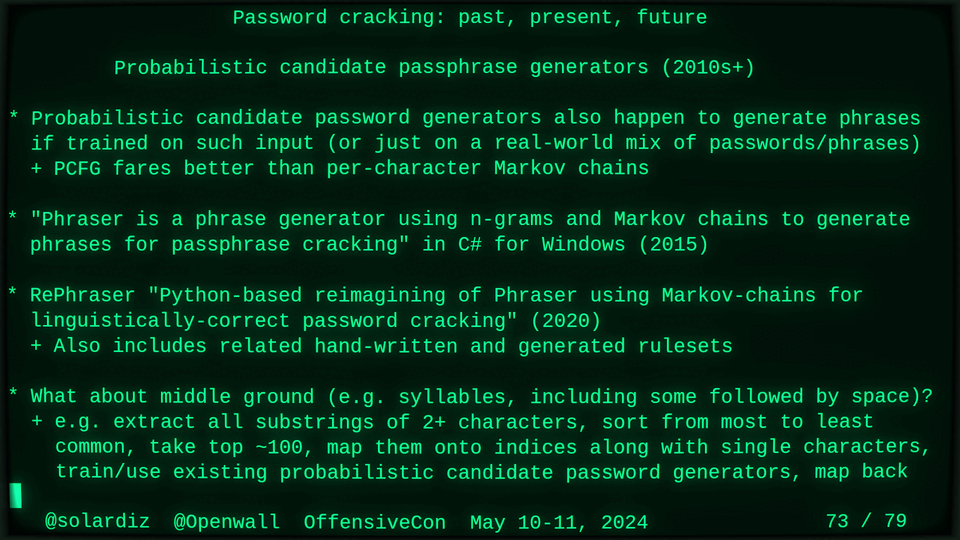
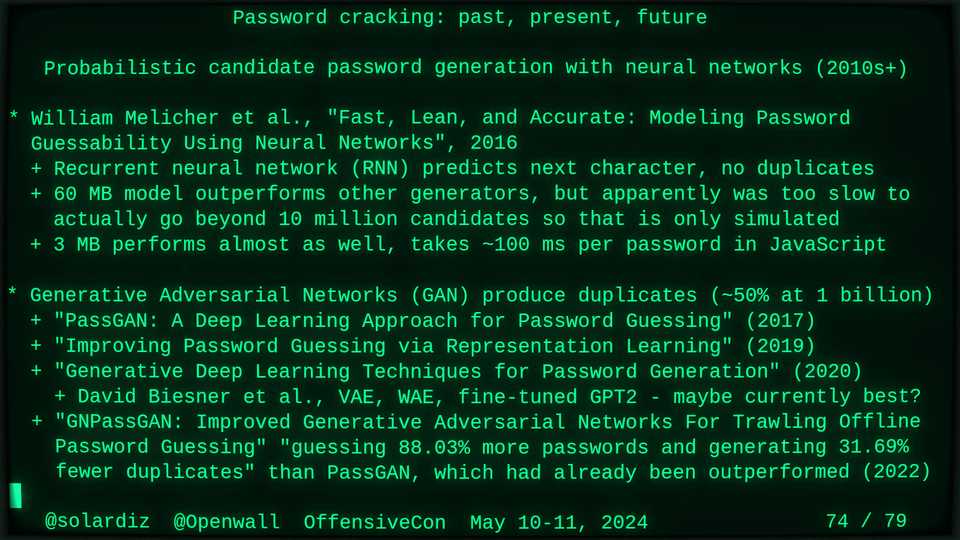
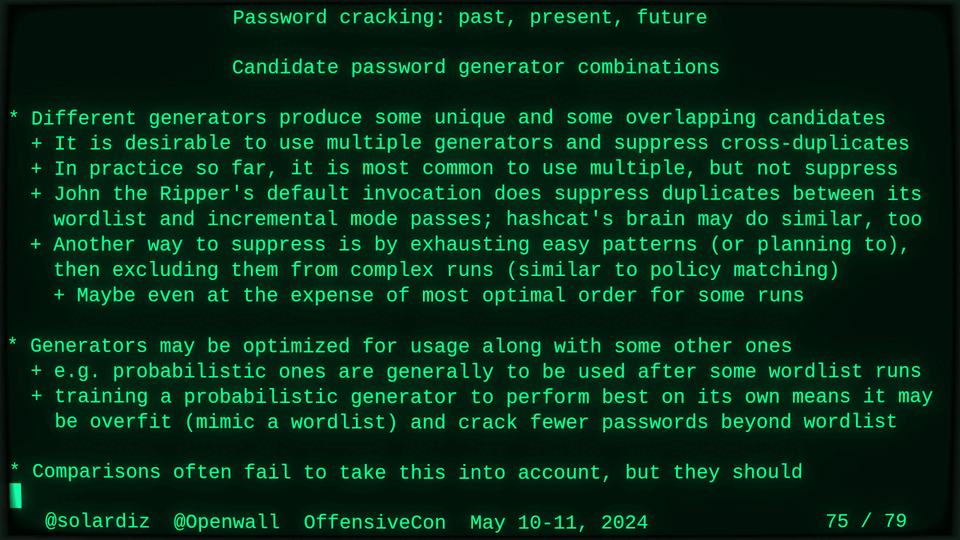
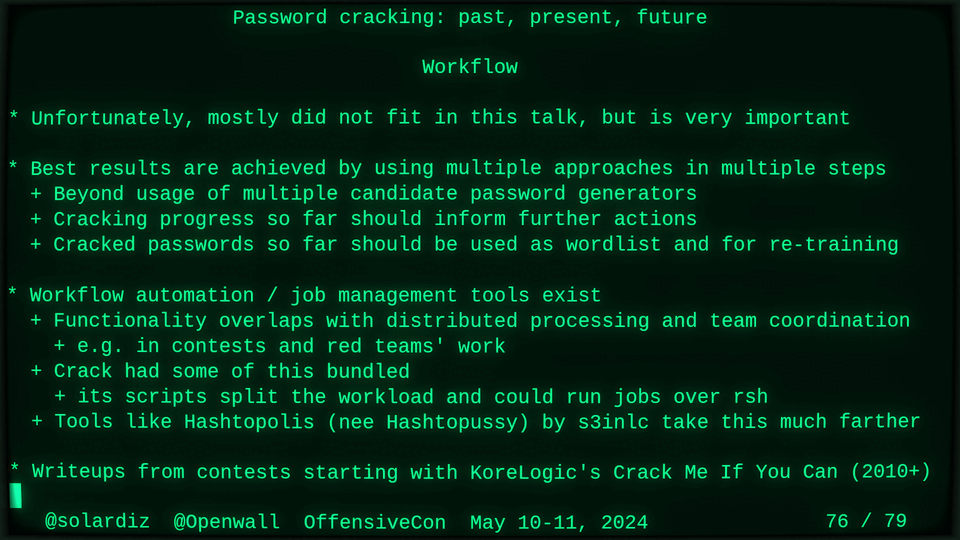
51115















































































