|
These are some screenshots of Owl-current live CDs for x86-64 and i686
as of 2012/08/18. Owl 3.1-stable (released later) looks similar.
The screenshots show how very conservative Owl is,
which is an advantage for some of our prospective users,
but a drawback for some others.
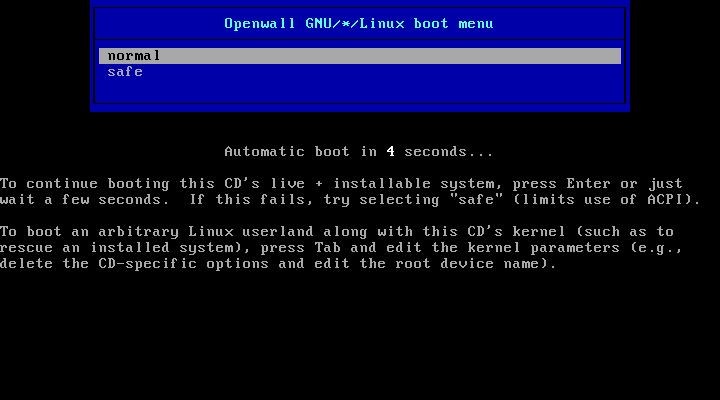
CD boot menu:
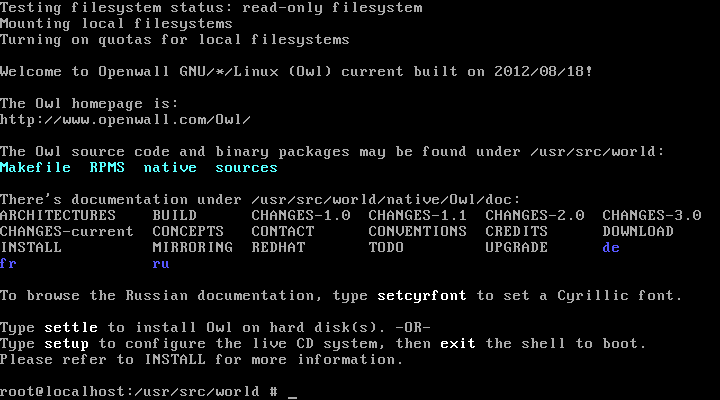
CD just booted up:
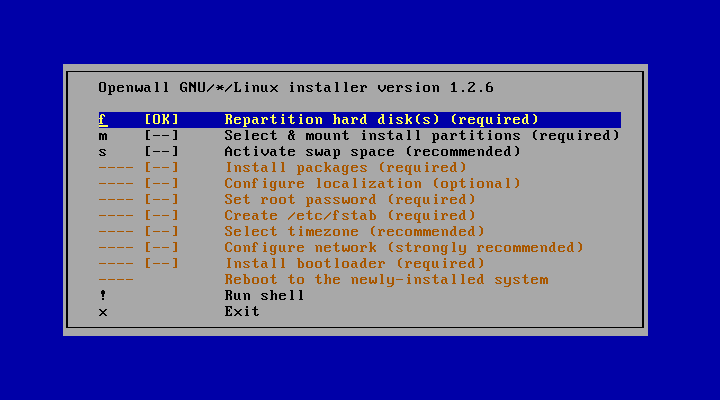
The installer program (settle):
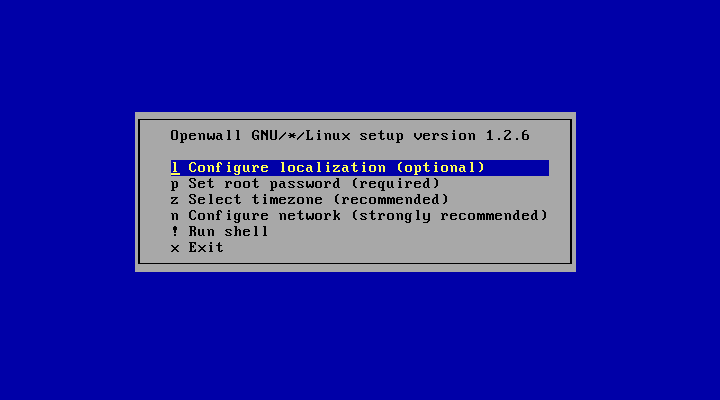
The system configuration program (setup):
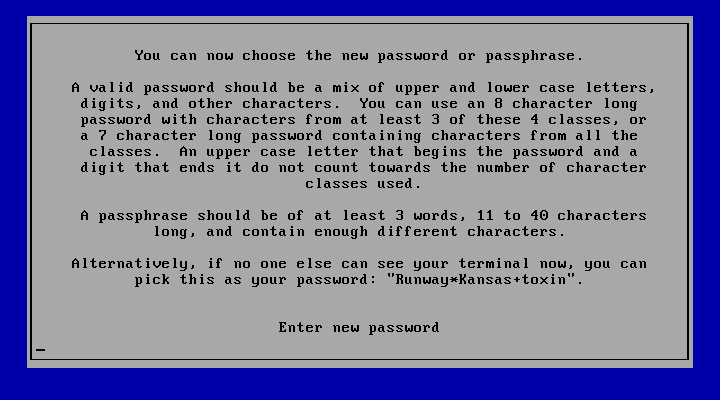
The password policy (configurable) is enforced even for the initial root password:
There are no SUID (set-user-ID) programs on Owl; there are only some SGIDs (set-group-ID):
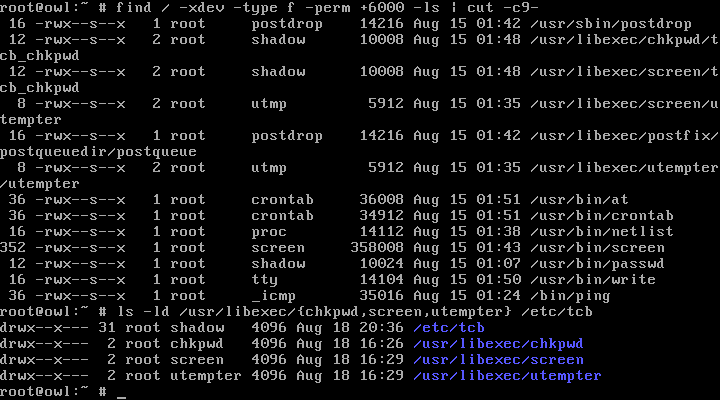
SGID programs, if the concept is used right, are a lower risk than SUID. In fact, many of these programs could be unprivileged, but having them SGID introduces a layer of security separation and deals with some minor and subtle attacks (such as a user bypassing password policy for their own account or mounting a local Denial-of-Service attack).
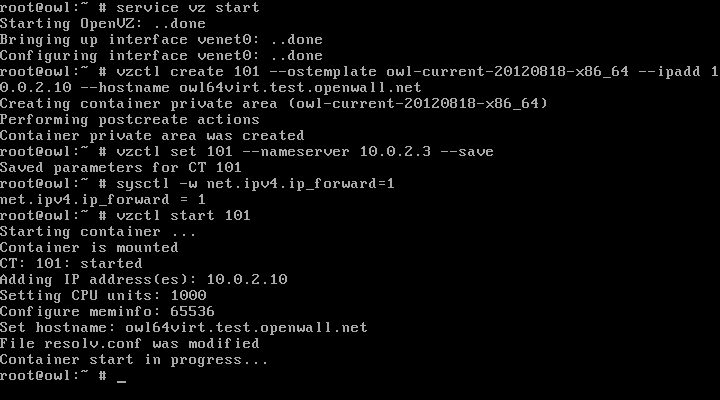
Starting the OpenVZ service and the first OpenVZ container:
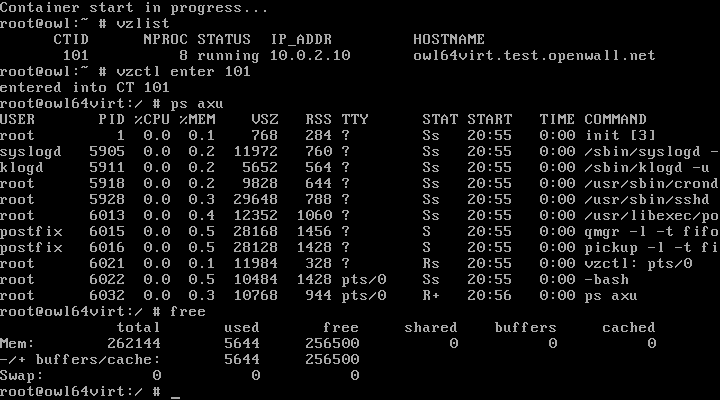
Listing the running OpenVZ containers and entering a container from the host:
Adjusting the limits on an OpenVZ container does not require its restart:
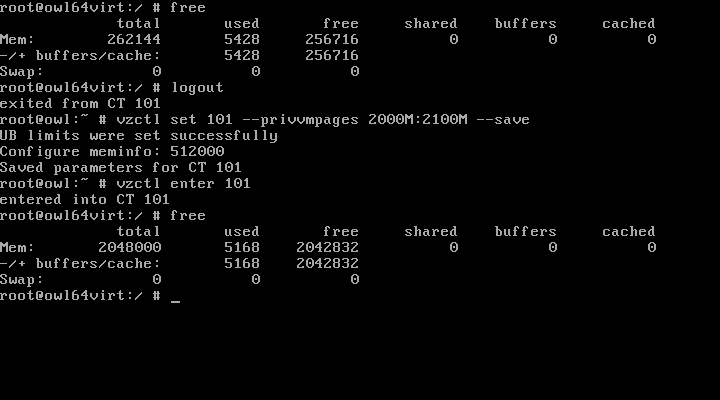
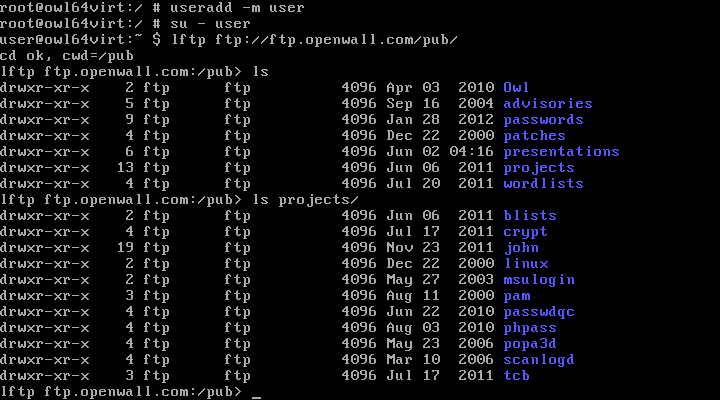
Networking from an OpenVZ container works just fine:
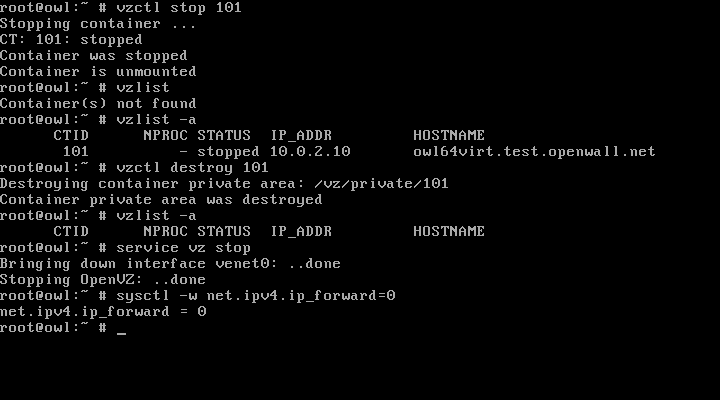
Stopping and destroying an OpenVZ container:
See also:
Openwall GNU/*/Linux presentation slides and
screenshots of passwdqc (our password/passphrase strength checking and policy enforcement toolset).
| 










